A Digital, Data-Driven Organization
While companies can have an excellent safety culture, cyber threats are always on the horizon. Trends in ICS cybersecurity have reported more unauthorized attempts and a marked increase in malicious code attacks. As a commercial off-the-shelf (COTS) software, ICS uses more and more hardware and software with IT technology being embedded (e.g., Windows operating system, ethernet IP-based communication, and virtualization such as VMWare and Hypervisor).
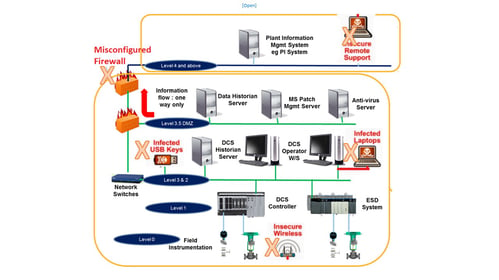
Implementing IP exposes ICS to the same vulnerabilities as IT. Common cyber incidences include blue screens, denial of service (DOS), and unauthorized remote access. Studies have shown that about 24% of cybersecurity threats come from insiders who inadvertently compromise businesses. Unknowingly, one can plug in an infected USB stick into a PCS computer and spread malware into plants, causing sometimes irreversible damage.
Therefore, aggressive education, training, visual management, audits, and the courage to give feedback to staff on PCS cybersecurity malpractices is surely needed. As part of an accelerated cybersecurity culture at the workplace, one must engage staff, conduct awareness training, and foster an understanding that becoming inactive and uneducated on cybersecurity risk management can lead to a major loss of business.
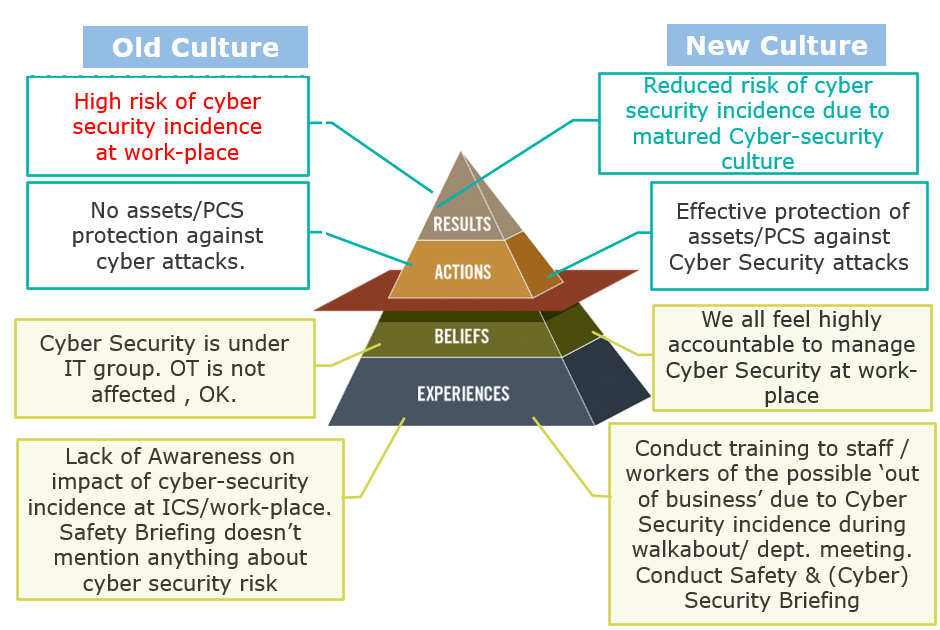
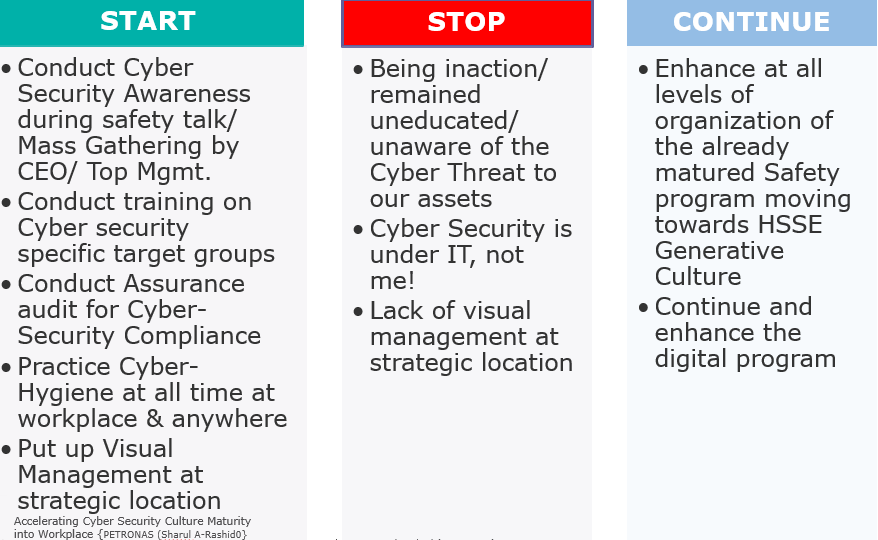
PETRONAS Use Case
For example, in the case of a threat from a phishing email, which accounts for more than 90% of cyberattacks, we at PETRONAS heavily engage our staff on human firewall campaigns. This includes not including confidential information in an email subject, logging out at the end of computer sessions, and periodically changing passwords. With a strong staff conviction, we further accelerate a matured cybersecurity culture at the workplace.
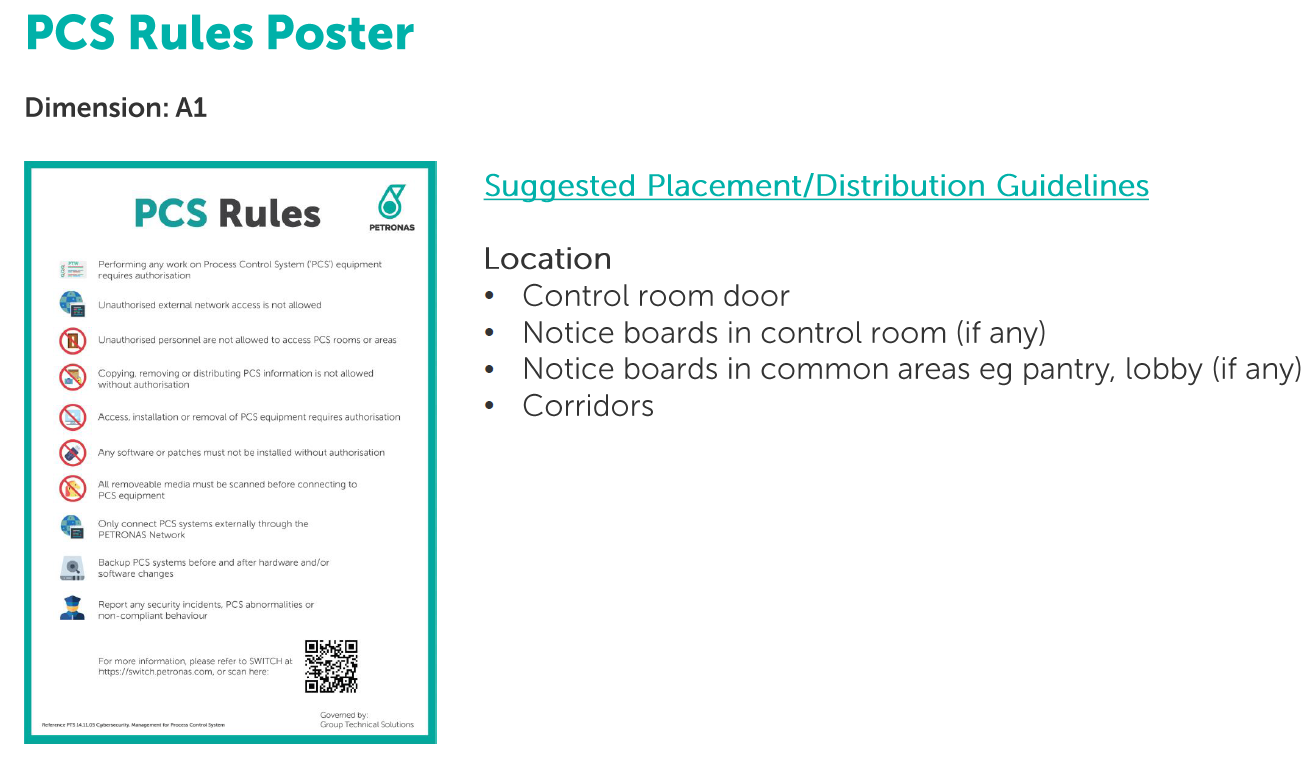
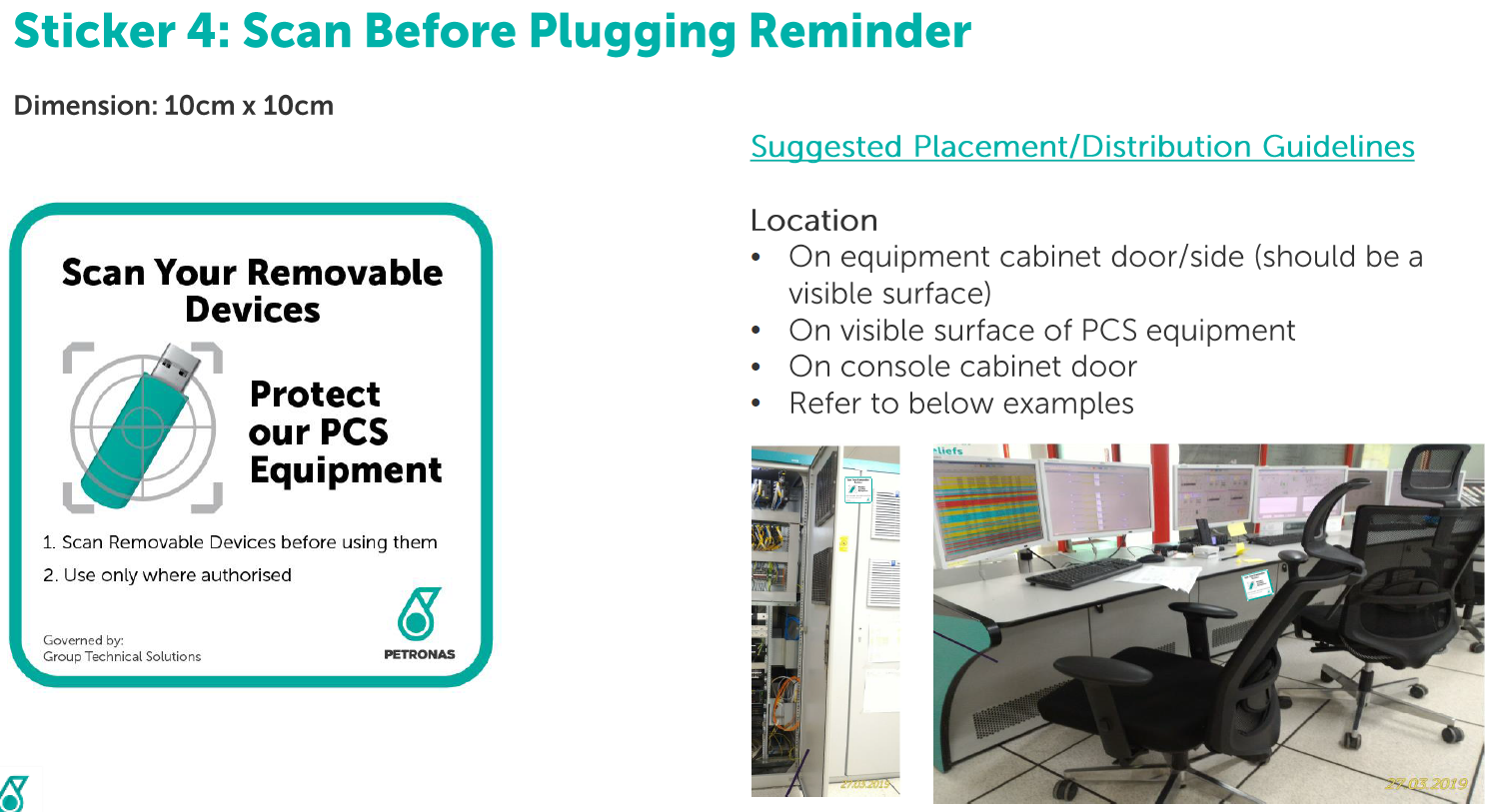
The followings images are exhibits of visual management, cybersecurity collaterals (OT stickers, PCS rules posters and cards) that are issued to all our sites at PETRONAS:



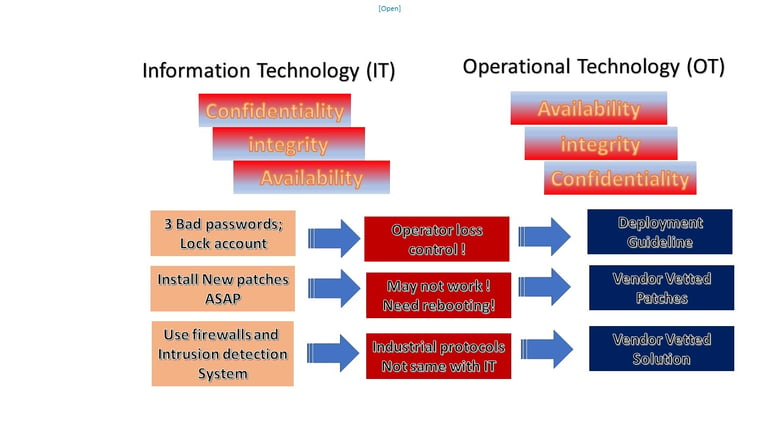
OT/IT Convergence
In leading the OT Cybersecurity team at PETRONAS, we engage and support staff as much as possible. We build and nurture our best performing teams with our new cybersecurity taskforce, as well as guide them using international standards best practices on sustainable, pragmatic approaches. The taskforce’s leadership ensures PETRONAS’ growth and sustainability, no matter what obstacles may come during the crafting and shaping of new outfits within the cybersecurity team.
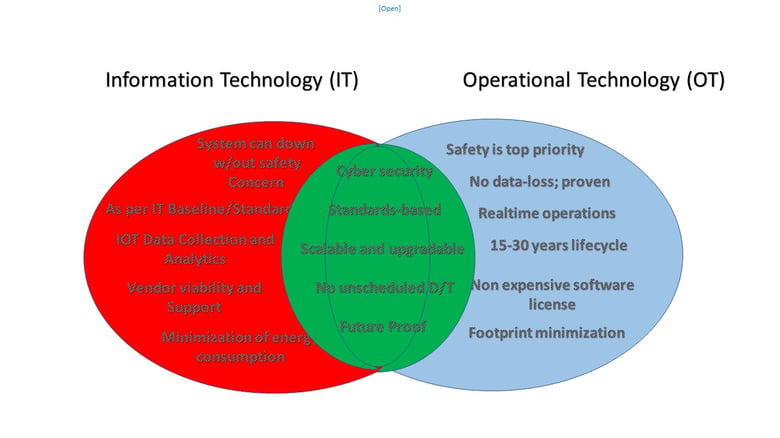
With IT/OT convergence, which requires cybersecurity to be looked at from a single enterprise lens, both our IT and OT staff are brought into the same classroom to share and learn from each other. During our classroom trainings on fundamental cybersecurity for ICS and IACS, for example, both IT and OT terminologies and priorities (such as confidentiality, integrity, and availability) are taught so that both teams can achieve commonality with our company KPIs. It is indeed a convergence in action when a nurtured trust is sowed for both departments which were previously siloed. Indeed, managing cybersecurity risks requires not only teamwork, but both alignment between processes and technology.
About the Authors
Sharul A. Rashid is the PETRONAS Group Technical Authority and Custodian Engineer, Instrument and Control. He is co-chair Certification Work Group (CWG) of Open Process Automation Forum (OPAF). He is also the Steering Committee (SC) member for JIP33 (IOGP) (International Oil & Gas Producer), the Vice-Chair ISAGCA (International Society Automation - Global Cybersecurity Alliance, Vice-Chair IASSC (Instrument Automation Standards Subcommittee) for IOGP. Additionally, he is the voting member for ISA-75 and IEC TC/S/15 for Smart Manufacturing. He is also Team Leader for Smart City project for PETRONAS. Sharul has more than 30 years of experience in handling instrumentation and control issues in oil & gas, gas liquefaction and petrochemical plant including pipeline transmission network. Sharul advises not only within his Group Technical Solution but also plant PETRONAS-wide on instrumentation and control issues. He involved as an instrumentation expert in many key PETRONAS projects e.g. Kertih Compressor Station, Peninsular Gas Utilization metering stations and MLNG Satu Rejuvenation and MLNG Dua Debottlenecking.
Azmi B. Hasim is Principal Engineer, Instrument and Control (I&C), in Group Technical Solutions (GTS), Petroliam Nasional Berhad (PETRONAS) since 2012. Previously he spent 17 years in Malaysian Refining Company Sdn Bhd as Electrical and Instrument Project Engineer and later as Staff Engineer, I&C. During his tenure, he lead Turnaround works for I&C field devices, a Group-wide line trainer, reviewer of company technical standards and has facilitated Instrumented Protective Function & Alarm Rationalization studies. Azmi currently leads Operational Technology (OT) Cyber Security governance across all PETRONAS sites and oversees deployment of OT cyber security solutions at all production sites. Azmi gained his Bachelor of Science in Electrical Engineering from Cornell University.




