Introduction
In the realm of cybersecurity, the significance of penetration testing and digital forensics can be likened to risk assessment. Without the latter, comprehending what needs safeguarding and the potential threats remains elusive. Risk assessment stands as the primary pillar, shedding light on the imperative need for protection. On the flip side, penetration testing—or ethical hacking— scrutinizes our IT or OT systems, simulating potential breaches and delineating courses of action should an attacker compromise the entire system. Concurrently, digital forensics unravels the intricacies of a compromised system, unveiling the attackers' methodologies and collecting evidence essential for legal action.
Understanding the pivotal role of penetration testing and digital forensics in cybersecurity aligns them shoulder-to-shoulder with risk assessment. However, in the domain of operational technologies (OT), challenges abound. Live OT system components pose real hazards during penetration testing, potentially causing harm to people and assets. Additionally, conducting digital forensics copies for all OT system hard drives becomes unfeasible during critical shutdowns resulting from cyberattacks, especially in critical sectors like oil and gas facilities.
As a consequence, many OT system owners opt to sidestep penetration testing and digital forensics, relying solely on risk assessment for their cybersecurity programs. Yet, this is not always the case. Regulatory requirements may compel organizations to implement these crucial activities, albeit with limited scope and budget. The apprehensions surrounding penetration testing, which might introduce operational risks, and digital forensics, causing system downtime for evidentiary collection, often lead organizations to resist their adoption. This reluctance holds true, reflecting industry needs and constraints.
However, the advent of AI technologies offers avenues to elevate the quality of penetration testing and digital forensics significantly. Let's delve into the specifics of each area to gain a comprehensive understanding.
OT Penetration Testing
Firstly, let's elucidate what penetration testing entails. It is a proactive process that simulates adversary attacks on target system components, enabling organizations to identify vulnerabilities and take corrective actions before real attacks occur.
In the context of IEC 62443, penetration testing is part of risk assessment, serving as a type of vulnerability assessment for OT. Detailed insights can be found in standards such as 62443-2-1 and 62443-3-2.
The methodology for conducting penetration testing varies, and of this article, we will adopt the simplified Penetration Testing Execution Standards (PTES). This framework consists of five phases: Reconnaissance, Scanning, Exploitation, Post-Exploitation, and Reporting.
Reconnaissance
Objective:
This phase aims to gather information about the target system, including systems details, network design, IPs, assets information, URLs, and people information.
Conducting Method using AI:
Typically, this phase involves using search engines, social engineering, and OSINT tools like Maltego and Recon-ng. AI can play a role in generating well-planned emails for active reconnaissance, enhancing the effectiveness of this phase.
Output:
Before moving to the next phase, an AI solution like ChatGPT can be employed to classify data, extracting relevant information for the scanning phase, such as IPs and ports.
Scanning
Objective:
The primary purpose is to identify vulnerabilities in the target system and analyze these vulnerabilities based on the information gathered during the reconnaissance phase.
Conducting Method using AI:
AI can be utilized in passive scanning, searching for the latest updates on specific services identified in the reconnaissance phase, such as Modbus. This approach is preferred for OT systems, minimizing the risk associated with direct scanning.
Output:
The result is the identification of the most critical vulnerabilities, guided by AI, for services like Modbus.
Exploitation and Post-Exploitation
These phases involve actual attacks, focusing on specific vulnerabilities identified, such as Modbus vulnerabilities. Activities may include testing possible attacks like shell command injections, guided by AI tools like Metasploit and ChatGPT. Exploration must occur in a controlled environment, adhering to legal permissions and isolated zones to prevent unintended consequences.
Reporting:
Final outcome of penetration testing necessitates meticulous documentation for both technical and non-technical audiences within the organization. AI solutions, like ChatGPT, can assist in structuring the final report.
Considerations during OT Penetration Testing:
- Emphasize that brute attacks and commands may need repetition for effective penetration. AI can expedite this process by generating custom commands.
- Highlight the importance of safeguarding organizational privacy and confidentiality when utilizing AI. Classify data appropriately to avoid unintended disclosure.
- Stress the necessity of obtaining legal permissions and approvals for tools and activities involved in penetration testing.
- Emphasize the need for a qualified and skilled team to undertake penetration testing tasks.
OT Digital Forensics:
Digital forensics is an integral part of cybersecurity incident response, often marking the initial phase in addressing incidents. It involves identifying the cause of incidents and collecting evidence for legal action, following standards like IEC 6244,3-2-1, and leveraging frameworks such as NIST SP 800-86.
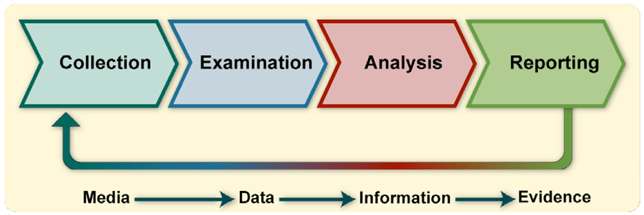
Source: NIST SP 800-86
Collection:
The collection phase, the first in the NIST framework for forensics, aims to gather forensic backups from target system machines to extract evidence for subsequent phases. Legal requirements surrounding the use of approved tools must be adhered to during this phase.
Examination and Analysis:
In these phases, the focus is on extracting and analyzing collected data to understand the nature of the attack. AI can act as an assistant in analyzing data patterns and recognizing attack patterns for more informed findings.
Reporting:
The final phase involves documenting findings and evidence as well as submitting them to legal and incident response teams according to organizational policies. AI can aid in structuring comprehensive reports.
Considerations during OT Digital Forensics:
- Acknowledge the legal nature of digital forensics and ensure that the use of evidence in AI is permitted by legal authorities to maintain its validity.
- Recognize the diverse types of digital forensics, such as network forensics, Windows forensics, malware forensics, and email forensics, and tailor tools accordingly.
- Understand that ethical hacking knowledge or penetration testing is a prerequisite for effective digital forensics, aiding in the analysis of attack patterns.
- Consider AI as a potential risk to privacy and evaluate its outputs carefully for validation.
Conclusion
Integrating AI in digital forensics and penetration testing for OT systems offers substantial benefits. These technologies, if used judiciously, can significantly reduce analysis time, enhance efficiency, and contribute to a more secure handling of OT systems. However, it is imperative to acknowledge the associated risks and potential drawbacks, such as legal issues and data leakage. As attackers increasingly employ AI, leveraging these technologies becomes paramount for fortifying cybersecurity practices in OT environments.



