Misconceptions about ICS/OT cybersecurity are stubborn. This "mythbusting" blog series dispels five common myths related to ICS cybersecurity. Catch up on the series if you're interested:
Now, let's dive in.
ICS Cybersecurity Myth #2
ICS networks use only proprietary systems/protocols, and attackers don’t understand these proprietary systems and protocols
Proprietary systems and protocols are usually designed and controlled by a single organization. Sensitive information about how these protocols are designed is not released for public use.
A common belief is that ICS protocols are proprietary, and that attackers don’t have access to—and don’t understand—ICS devices and proprietary protocols. This belief can lead to a false sense of security.
Busting ICS Cybersecurity Myth #2
Although hacking ICS devices may be challenging due to their proprietary nature, threat actors behind targeted attacks are usually knowledgeable, persistent, and resourceful—in many cases, sponsored by nation states.
While proprietary in nature, many ICS vendors use open-source software in their ICS products. A recent report by Black Duck revealed that 96% of applications reviewed contained open-source components, and 78% of the codebases examined had at least one vulnerability. The average number of codebase vulnerabilities was 64.
With newer-generation ICS systems, there is a trend of using common IT protocols in ICS that further exposes ICS to cyberattacks. The SMB protocol is widely used across IT as well OT networks.
Attackers also can buy ICS systems and readily available malware from the darknet (the black market, or malware-as-a-service) to play in their labs. For some insightful stories about the darknet and cybercrime, check out the podcast Darknet Diaries.
The TRITON Malware Attack
The TRITON malware attack targeted an industrial organization in the Middle East. The TRITON malware (also called TRISIS) was used to target a safety instrumented system (SIS) from Schneider Electric called Triconex. Attackers demonstrated their capabilities to compromise a proprietary system and communication protocol called TriStation.
The attackers deployed TRITON shortly after gaining access to the SIS, indicating that they had pre-built and tested the tool—which would require access to hardware and software that is not widely available.
Although not explicitly designed to target ICS, WannaCry (May 2017) impacted ICS as well.
ICS Incidents on the Rise
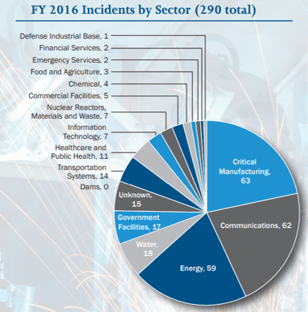 Diagram courtesy of the author
Diagram courtesy of the author
ICS incidents are on the rise, as shown by the chart (incidents tracked by ICS-CERT).
According to CyberX, 82% of industrial sites depended on remote management protocols like RDP and SSH in 2017. Not only are hackers familiar with these access protocols and their vulnerabilities, they are even familiar with proprietary ICS systems. Attackers can easily find vulnerabilities within critical infrastructure with open-source software tools.
At a recent Pwn2Own event organized by S4, hackers demonstrated numerous exploits in ICS platforms that are used within the manufacturing, heavy industry, and critical infrastructure sectors.
The proprietary nature of systems and protocols in ICS networks is not a deterrent to attackers.
Stay tuned for the next part in this series, in which we break down Myth #3: the belief that ICS is protected from cyberattacks because there is a firewall between the ICS network and other networks.
Interested in reading more articles like this? Subscribe to the ISAGCA blog and receive weekly emails with links to the latest thought leadership, tips, research, and other insights from automation cybersecurity leaders.




