The following blog is adapted from the book Industrial Cybersecurity Case Studies and Best Practices, authored by Steve Mustard. More excerpts will be following in the coming weeks. See Excerpt #2 here. See Excerpt #3 here.
NEW: See Steve Mustard's October 2022 appearance on NasdaqTV here.
Measure to Manage Risk
Another Cybersecurity Awareness Month is upon us, and there is no better time to consider how well we are collectively managing cybersecurity risk in industrial facilities, in particular:
- Managing industrial cybersecurity risk
- Quantifying the likelihood of a cybersecurity incident
- Applying risk reduction
- Maintaining cybersecurity risk to as low as reasonably practicable (ALARP).
Managing Industrial Cybersecurity Risk
There is now a greater appreciation of the difference between industrial cybersecurity risk and its IT counterpart. Despite this, many organizations still use the same techniques to estimate industrial cybersecurity risk.
Industrial cybersecurity risks are unique, as they combine threats related to information security (destructive malware, DoS attacks) with the consequences related to safety (death or injury, harm to the environment, damage to equipment), as shown in the example risk matrix in Figure 1. It therefore makes more sense to apply the principles of safety risk management.
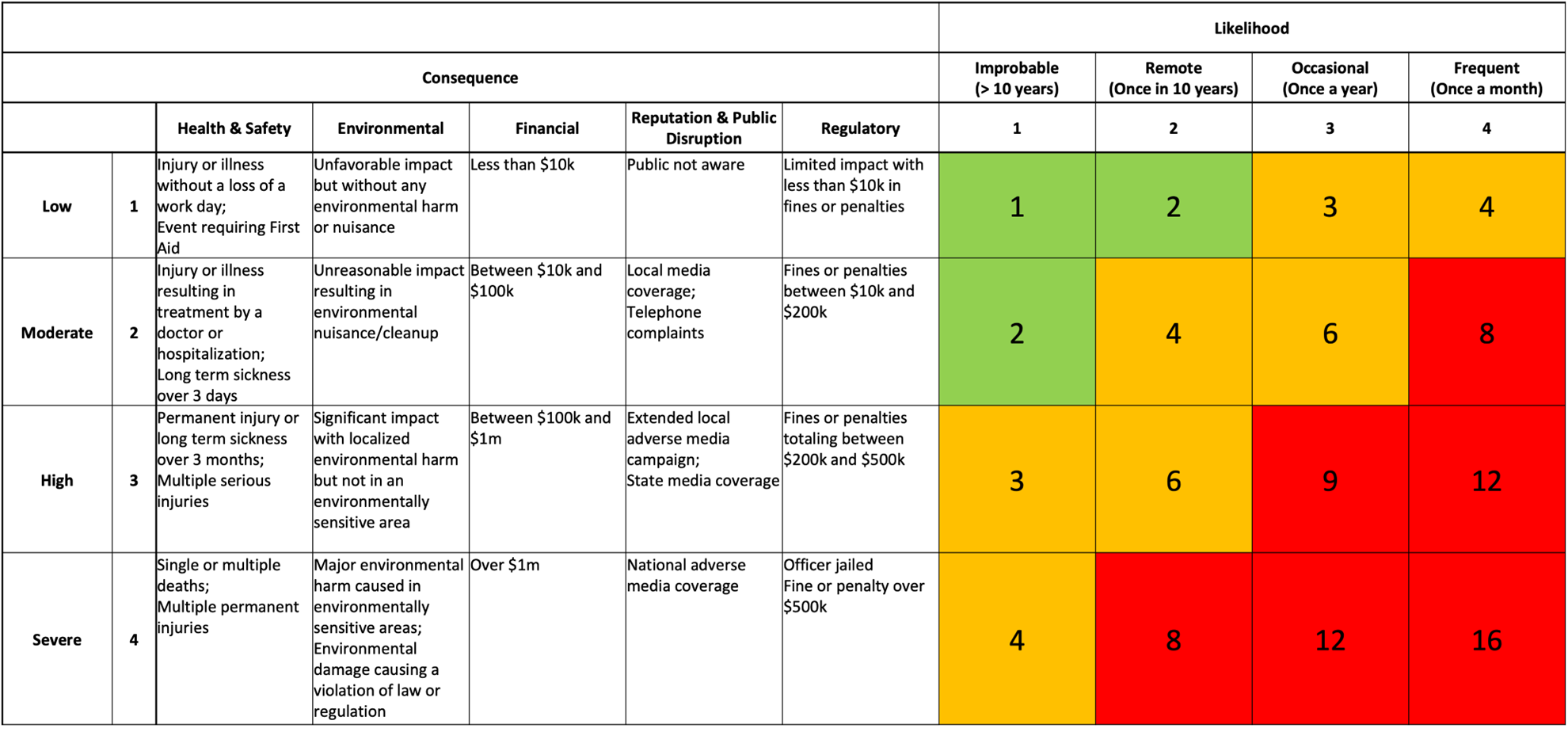 Figure 1: Example Risk Matrix
Figure 1: Example Risk Matrix
Edward Marszal and Jim McGlone have developed a solution to ensure that industrial cybersecurity risks are treated in the same way as safety risks: the security PHA review, or SPR (pronounced spur). Their book Security PHA Review for Consequence-Based Cybersecurity[1] highlights the limitations of existing cybersecurity risk assessment methodologies and details the SPR methodology. SPR reuses the principles of safety risk assessment already in place. As the authors note: “the process industries have already established methods for risk assessment that have been successfully in use for decades. The optimal solution for assessment of cybersecurity risks is not to start from scratch with new studies but to extend the existing studies to incorporate new objectives and requirements.”[2]
Estimating Likelihood
A common theme in cybersecurity is the reluctance to use probability and statistics to estimate cybersecurity incidents. As a result, organizations tend to underestimate the likelihood of a cybersecurity incident, and therefore fail to apply sufficient effort to reduce the risk.
On the surface, the lack of historical data seems to make it difficult to analyze and provide reliable estimates of future incidents. Douglas Hubbard and Richard Seiersen offer methods to provide qualified estimates in their book How to Measure Anything in Cybersecurity Risk. Contrary to the concerns about estimating risk, they point out: “There are problems in statistics that can only be solved by using a probabilistically expressed prior state of uncertainty.”[3]
Monte Carlo simulation was created to help estimate events with no prior history. Bayes’s theorem enables the prediction (with appropriate confidence interval) based on any data sample size. Both can be used to provide estimates that can better target risk reduction efforts.
Risk Reduction
Risk reduction is ultimately about identifying and applying controls to reduce the likelihood and/or consequence of a cybersecurity incident. The ISA/IEC 62443 Series of Standards provides an excellent framework on which to define cybersecurity controls using clear and consistent language. The standards also define all the stakeholders that are involved in cybersecurity management. These include the asset owner, maintenance service provider, integration service provider, and product supplier. It is essential to identify the responsibility for cybersecurity controls, especially as this responsibility is often shared among multiple stakeholders. The ISA Global Cybersecurity Alliance (ISAGCA) is a collaborative forum to advance cybersecurity awareness, education, readiness, and knowledge sharing. One key area of focus for ISAGCA is to provide guidance to industry on how to apply the ISA/IEC 62443 standards.
Even without doing a thorough risk analysis, it is still possible to apply some basic controls and make a significant improvement in cybersecurity posture. Examples abound: secure network design, hardening of devices, deployment of antivirus software, ongoing update of operating system patches, maintenance of system backups, establishment of recovery procedures, establishment of awareness training for all personnel, and establishment of cybersecurity incident response plans. These basic controls are like the safety rules that many organizations operate.
One way to highlight the importance of these controls is to develop a cybersecurity bowtie, such as that shown in Figure 2. Bowtie diagrams are commonly used to identify the preventative and mitigating controls (or barriers) that must be in place to manage safe operations. Identifying the barriers that must be in place to manage cybersecurity risks using a bowtie diagram can help to elevate the significance of the associated controls, and by introducing routine checks of barrier status can help address any gaps in a more systematic manner.
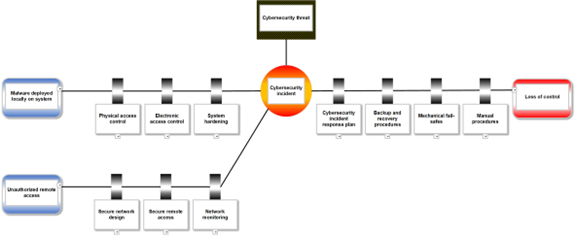 Figure 2: Cybersecurity Bowtie Diagram
Figure 2: Cybersecurity Bowtie Diagram
ALARP
The phrase as low as reasonably practicable (ALARP) originates from health and safety legislation developed in the UK. ALARP is widely used in safety standards and legislation throughout the world. IEC 61508[4] defines the following for risks:
- Zero risk can never be reached; only probabilities can be reduced.
- Non-tolerable risks must be reduced (ALARP).
- Optimal, cost-effective safety is achieved when addressed in the entire safety lifecycle.
Figure 3 shows a visual representation of ALARP. Initially minimal cost (or effort equated to cost) is expended to mitigate significant or intolerable risk. As risk is addressed, the cost to mitigate increases further. The ALARP point is when the cost to mitigate additional risk becomes disproportional to the risk reduction.
The ALARP concept can be applied equally well to managing cybersecurity risk, and especially to industrial cybersecurity risk. Consider the fact that investment in cybersecurity spending is forecasted to reach $172 billion in 2022[5] Despite this massive investment, organizations are still being impacted by cybersecurity incidents that, with hindsight, could have been easily prevented. Examples include: The fuel pipeline company that was incapacitated by ransomware because of an inadequately secured remote access connection; the water treatment plant that was tampered with by a disgruntled former employee who still had access to systems; the compromise of a safety controller that could have been prevented by turning a physical key to a different position.
These incidents illustrate the fact that too little effort is made to address intolerable risks that, ironically, involve minimal cost. While it is unclear if the current investment is appropriate, it is clearly not correctly targeted.
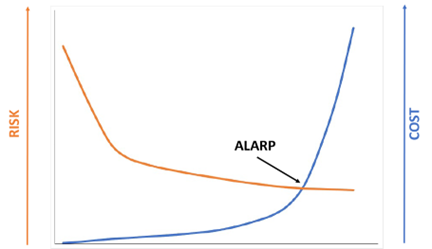 Figure 3: Visualizing ALARP
Figure 3: Visualizing ALARP
Summary
Now that organizations have a better understanding of the difference between industrial cybersecurity and IT cybersecurity, there is an opportunity to apply existing proven industrial risk management practices. The use of statistical methods can provide a more reliable estimate of the likelihood of a cybersecurity incident. This more reliable estimate can be used to better identify the risk reduction needed to manage the risk to as low as reasonably practicable (ALARP). The use of existing tools such as bowtie diagrams can help to elevate the significance of controls needed to maintain a secure industrial facility. “The optimal solution for assessment of cybersecurity risks is not to start from scratch with new studies but to extend the existing studies to incorporate new objectives and requirements.”[6]
[1] Edward Marszal and Jim McGlone, Security PHA Review for Consequence-Based Cybersecurity (Research Triangle Park, NC: ISA [International Society of Automation], 2019).
[2] Marszal and McGlone, Security PHA Review for Consequence-Based Cybersecurity, 14.
[3] Douglas W. Hubbard and Richard Seiersen, How to Measure Anything in Cybersecurity Risk (Hoboken, NJ: John Wiley & Sons, 2016), 38.
[4] IEC 61508-1:2010, Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems – Part 1: General Requirements (IEC [International Electrotechnical Commission]).
[5] " Cybersecurity spending trends for 2022: Investing in the future”, CSO, Accessed February 14, 2022, https://www.csoonline.com/article/3645091/cybersecurity-spending-trends-for-2022-investing-in-the-future.html
[6] Marszal and McGlone, Security PHA Review for Consequence-Based Cybersecurity, 14.




