The adoption of Industry 4.0 technologies is increasing efficiency and profitability across industrial control system (ICS) environments, making data available from myriad sources, and employing advanced software tools to analyze information. This gives plant staff insights for facility and machine optimization at a rate never before experienced in industry.
This increase in data is attributed to Industrial Internet of Things (IIoT) sensors and data processing engines everywhere—inside and around machines within the shop, in remote field locations, at the edge of factory control networks, and in the cloud. The interconnectedness of these components helps generate accurate and beneficial insights.
Though the benefits are numerous, connecting an enterprise of ICS devices while maintaining security is no easy task. Where interconnected components exist—especially involving the cloud—so do opportunities for downtime, data theft, and other kinds of malicious cyberattacks. But through careful planning and implementation, and using modern cyber-physical protection systems, users can leverage the benefits of the IIoT while defending their networks, devices, and data from intrusion.
Modern ICS challenges
IIoT devices generate data throughout the enterprise, which helps users make better-informed operational decisions. But many are hesitant to connect every facet of their plant and implement Industry 4.0 trends because of the risks of exposing previously isolated devices.
A 2018 application and network security study by Radware revealed the average cost of a penetrating cyberattack is a staggering $1.1 million. In addition to being a major financial and business continuity disruption, a cyberattack can erode confidence and public trust, critical factors in today’s business landscape.
Users are left with a conundrum: If they do not connect their plants, they miss out on cloud services, remote connectivity, and increased contextual access to data on the factory floor—and therefore on more benefits for operational efficiency and simplicity. But they are rightfully concerned that to reap these benefits and improve productivity, they risk exposing their facilities to cyberattacks.
Fortunately, there are tools to achieve these benefits while mounting a strong defense against cyberattacks. Implementing network monitoring and artificial intelligence–driven threat detection systems is a positive start to cyberattack reduction and mitigation, but these do not go far enough to address modern-day cyberthreats to operational technology (OT) systems. These software systems are adept at detecting and alerting administrators about suspicious network activity, and in some cases blocking it, but remediation capabilities are debilitatingly limited.
When a cyberattack gets through, there is not much—if anything—these systems can do to kill the threat and control damage to the OT environment. They typically rely on human intervention to shut off hackers’ connections to the network and to reclaim machine and process control.
By integrating cyberthreat detection tools with programmable logic controller (PLC) code to act during an attack, programmers build in the protection and assurances needed to safely connect a plant. This type of cyber-physical incident response solution responds to threat detection by intelligently maintaining uptime of noninfected production cells when possible. Meanwhile, it places infected components into a safe physical state and quarantines them from the rest of the network, shutting down bad actors’ access into the system.
Experience centers educate visitors
Although cyber-physical protection systems can provide robust protection and mitigate risk, deploying them properly requires a thorough understanding of ICS cybersecurity best practices. To help users develop these skills, visitors of hands-on manufacturing experience centers are taught methods for connecting devices securely, showcasing the benefits of integrating cyber-physical protection systems into real-world production lines.
Demonstration systems, on a most basic level, flash warning lights and sound alarms when a simulated intrusion takes place. Using human-machine interface displays, visitors witness more advanced actions, such as dynamic firewall rules isolating infected zones, while PLCs place physical equipment into safe states. These systems also demonstrate access control via radio frequency identification and password login, with some users limited to accessing certain areas of the plant, and other users limited to different areas.
 Figure 1. Zero-trust stance. Recent events show cyberattacks can come from external or internal threats, prompting designers to adopt a zero-trust stance for ICS environments, where every network device and user must authenticate.
Figure 1. Zero-trust stance. Recent events show cyberattacks can come from external or internal threats, prompting designers to adopt a zero-trust stance for ICS environments, where every network device and user must authenticate.
Manufacturing industries are recognizing that threats do not only come from outside an organization, but they can also come from within it. They are consequently moving to a “zero-trust” stance (figure 1). They must watch and secure traffic on the local network, in addition to monitoring traffic coming in and leaving the network, and every user and device with network access must be authenticated.
Defense-in-depth
To reliably protect a network, it is necessary to implement defense-in-depth (DiD). This strategy focuses on creating multiple layers of security, so in case one fails, others remain to protect a facility and its assets.
As a physical example, DiD can be related to the types of security found in most homes and offices. The front door locking mechanism acts as the outer layer of security. To access the next layer in, residents and visitors must authenticate via key, Bluetooth, fob, or another means of entry. Once inside, there are likely multiple rooms, each containing separate assets and topics of information. These rooms can be locked, restricting entry again only to those with the appropriate clearance. This protects most of the structure if one or more rooms become compromised.
Analogously to rooms in a home or office, factories are made up of individual cells, each performing a specific task for producing finished goods. Each cell shares information with units inside the cell and with a limited number of carefully monitored data exchanges across cells. Intercell data sharing requires authentication, helping to protect information and machine control from falling into the wrong hands.
There are three pillars of DiD:
- Plant security: maintaining control at a facility’s cyber- and physical boundaries, determining who and what are allowed in and out. This refers to personnel, devices, and information.
- Network security: limiting network and port access to verified and trusted devices that are supposed to transmit data through these mediums. Cyber-physical protection systems ensure network security is maintained, and they sound an alarm and even act in the event of intrusion.
- System integrity: protecting individual devices from compromise. Integrated security features in control devices help provide protection against unauthorized configuration changes and can further resist the ability of bad actors to navigate a plant network.
Layered security through DiD is the linchpin of implementing industrial cybersecurity safeguards. Integrated enterprises and facilities must maintain strong firewall rules, only allowing necessary traffic between information technology (IT) and OT networks, and among cell areas on the plant floor. Requiring certificates and authentication to access networks and devices adds another layer of security that hackers must overcome to gain control.
Additional safeguards
Deploying network segmentation by location and cell area helps isolate security breaches if they do arise, limiting the spread of malware infection or equipment control compromise. By contrast, flat and nonsegmented networks allow infection to spread much more quickly and with much less visibility to facility personnel.
In addition, many modern PLCs and intelligent IIoT devices have onboard encryption capabilities. Facility staff should ensure these functions are enabled and used, though individual device protection is no substitute for safeguarding network infrastructure. For secure remote connection to machines and plants, it is recommended to use and manage secure virtual private network tunnel connections.
With these and other safeguards in place, users strongly increase their defenses against cyberattacks from within and without plant boundaries. But the threat is always present no matter how well prepared an organization is.
Cyber-physical protection systems help reduce the frequency and severity of cyberattacks in sensitive ICS environments by using threat-detection software platforms of user choice, and programming response actions directly into PLC logic. In a security event, firewalls and switches within the architecture self-adjust access rules to shut down the bad actor’s connectivity, while PLCs act directly on process equipment to place potentially affected cell areas into a predetermined safe state, which is often but not necessarily always “off.”
Further factory integration
Designing and programming effective cyber-physical protection systems takes time, collaboration, and a strong understanding of system requirements—especially when passing data between IT and OT networks and using the cloud for remote access and data analytics.
Hands-on experience centers showcase cloud-edge integration in a standard factory floor automation portfolio, giving visitors practical examples of the defense-in-depth concept deployed on a production line. Visitors can observe the steps a cyber-physical incident response system takes while responding to a cyberthreat, with the same PLCs driving robots and other machines used to execute safety logic sequences.
These interactive facilities are technology and brand agnostic, so visitors witness tech from different vendors, which is what most factories look like. The cyber-physical response demonstrations and other core ICS security considerations are applicable to all vertical industries throughout discrete and process automation.
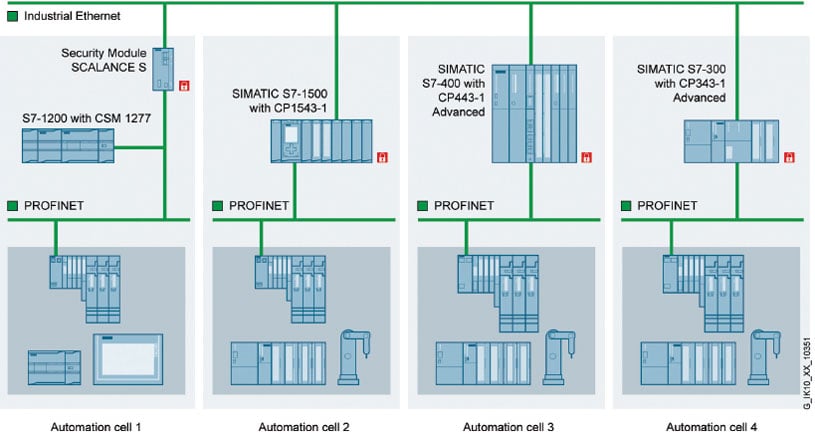
Figure 2. Segmenting a network. By segmenting a network and limiting traffic among various cell areas—a concept demonstrated for visitors at Siemens’ hands-on DEX center—users mitigate the risk of cyberattacks.
In conjunction with a local manufacturing research group, Siemens recently equipped and is opening a hands-on digital enterprise experience (DEX) center showcasing the DiD approach, along with simulated threat detection and response. At this DEX center, Siemens conducts hands-on workshops across a multitude of Industry 4.0 technology topics, driven by user interest. The demonstrated production line focuses on educating DEX center visitors on the importance of access control and a segmented network architecture to protect individual cell areas from other potentially compromised cells during an attack (figure 2).
Considering methodologies for plant, network, and device cyber-protection, users should be emboldened to install IIoT technologies throughout their enterprises. By building out cybersecurity defense-in-depth, plant managers are preparing their facilities for a host of digital operation and production enhancements.
Regardless of skill level, tapping outside help and attending hands-on sessions in an ICS environment can help equip users with the skillsets they need to efficiently safeguard their facilities from intrusion. This also brings operational peace of mind, knowing automated responses are configured and ready to act. Careful design and deployment let companies gain the benefits of IIoT data and analysis reliably and securely.
All figures courtesy of Siemens Industry Inc.
This blog has been repurposed from InTech.