The Industrial Internet of Things (IIoT) refers to systems that connect and integrate Industrial Control Systems (ICS) with enterprise systems and the internet, enabling digital transformation. IIoT-based implementations provide numerous benefits, including greater access to data, efficiencies of scale, and more; however, they can also provide opportunities for downtime, data theft, and other kinds of malicious cyberattacks. Companies and organizations that have adopted IIoT, analytics, and cloud computing consistently report an overall positive impact on traditional operational technology (OT)/ICS secure network architectures and have found that the Purdue Model–a key structural model for ICS security defined in ISA/IEC 62443 – has continued to be applicable to IIoT-based implementations. Below, you'll read about cybersecurity recommendations for IIoT.
What is the IIoT?
The Internet of Things (IoT) has revolutionized the way information is shared and managed. Today, IIoT is being embraced by various industries including oil and gas, manufacturing, healthcare, logistics, and transportation to enhance productivity and efficiency. IIoT applications are used for asset tracking and management, predictive maintenance, energy-saving, and quality control.
IIoT adoption is increasing efficiency and profitability across ICS environments with sensors, making data available inside and around machines. Extensive data points with advanced computing environments are rapidly transforming network perimeters, including mobile devices, cloud applications, and platforms.
Cloud computing provides virtualized platforms with elastic compute and storage capabilities. Cloud platforms are usually run as a service- based enterprise on large data centers that make it possible to easily acquire additional computational (e.g., CPUs) and storage capacity (i.e., disk space) as needed. This can entirely remove the need for a software-based enterprise to acquire and manage their own computing infrastructure.
IIoT Security Planning
IoT security planning starts with a cyber-risk assessment, however not all IIoT deployments pose threats to the physical world. Sending OT data to the cloud for analysis and analytics without sending commands back to the industrial control system is one example. This process is often called an “open loop” operations, which is easy to manage and secure since there is one-way communication from edge to cloud.
When deploying hardware that is only physically able to monitor but not control anything, we generally face only conventional business risks. Conventional security principles apply, and direct connectivity to enterprise—and even cellular and internet networks—is appropriate. Cyber risk assessment for system design determines the scope of the risk by partitioning the system under consideration (SUC) into separate zones and conduits. The intent is to identify assets that share common security characteristics in order to establish a set of common security requirements that reduce cybersecurity risk.
Partitioning the SUC into zones and conduits can also reduce overall risk by limiting the impact of a cyber incident. Incident likelihood can be estimated by decomposing threats and vulnerabilities and using semi-quantitative methods directly to the internet or a cell network. IIoT technologies have also introduced new gateway devices that can be used with local human-machine interface (HMI) assets and send industrial assets and machine data to the cloud.
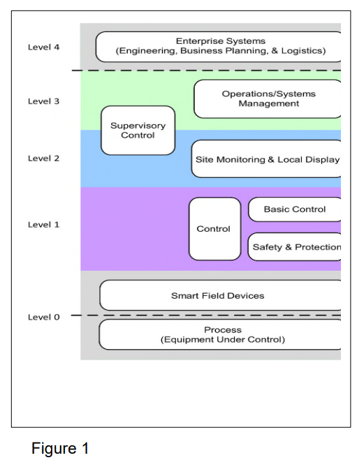
The adoption of several new technologies has posed challenges for the Purdue Model, whose main goal is to throttle or prevent data traffic between levels. The Purdue Model is shown below in figure 1, where data from sensor in the field at level 0 reaches enterprise systems in level 4 via controller in level 1, and operator workstation in level 2/3. However, IIoT allows devices to communicate through an IoT gateway or even directly with cloud services.
Typical IIoT architecture is shown below in figure 2. This architecture provides an overview of the general structure of the IIoT based systems, and there could be variations. For example, in some cases cloud environment may be deployed on premise. IIoT has only two levels–edge and Cloud. Levels 1 and 2 of the Purdue Model becomes edge in IIoT model, and levels 3 and 4 of the Purdue Model–which is business planning–becomes cloud. Note that levels can be moved to edge to improve performance and reliability or can be moved to cloud making it easier to install, scale up, upgrade, and more.
Countermeasure
Cloud-connected network resources like edge gateways, software, and devices need to be hardened to reduce the risk of inadvertent access. Credentials and permissions to access local resources from cloud -connected resources should be managed to limit the scope of impact of an adverse event.
While specific hardening guidelines are dependent on the edge gateway’s operating system, general guidelines to harden and securely configure an operating system include a multitude of things. Some examples include removing unnecessary service, applications, and network protocols, configuring operating system user authentication (removing unneeded accounts, disabling noninteractive accounts, configuring automatic time synchronization), configuring resource controls appropriately (allowing access to only needed resources), installing and configure additional security control (anti-malware, intrusion detection, and host-based firewalls).
Access to unnecessary hardware ports like USB and serial should also be disabled using both physical and software means. In the case of edge gateways, it’s important to check the vendor’s documentation to ensure that appropriate steps have been taken to harden the operating system.

Network Design
The Purdue Model has been a mainstay of automation and control systems for 30 years. This model is utilized when considering cybersecurity of ICS by implementing network segmentation and perimeter-based security controls to separate business and control networks to mitigate risk. Some have found this model to be challenging to apply to IIoT scenarios, as these architectures connect industrial sensors.
Cloud Provided Security
Critical elements for consideration include:
- Services such as VPNs (Virtual Private Network) or other secure communication capabilities for communications including a service to convert insecure automation protocols into secure communication protocols before transmission. Capabilities to assist in protecting data availability, integrity, privacy, and confidentiality including use of encryption for data in transit and at rest
- Identity management capabilities, which include both the management of identity for devices as well as authentication and authorization for user access
- Rights management capabilities to control access and authorization within the cloud
- Capability for asset owners to establish residency controls for data in the cloud
- Audit and monitoring capabilities including the ability to centrally log events and provide This also includes threat detection and behavior anomalies. Monitoring solution shall also create an industrial network traffic baseline and monitor anomalies and adherence to the baseline. Testing to be periodically to test devices and OT systems, edge gateways, networks and communication and cloud services
- Capabilities to supplement asset owner’s incident response activities
- Patching capabilities because as the adoption and complexity of software increases, so does the number of defects—some of which will be exploitable vulnerabilities. While eliminating vulnerabilities, prioritize by criticality by patching the most critical assets first. During design stage mechanisms shall be created to identify, network isolate and/or replace legacy devices and IIoT systems that are not capable of receiving updates
- Capability to identify anomalies to gain insights on complex events which can be used to improve the security posture which will help to detect and respond to incidents in a timely manner
- Capabilities for backup and recovery
Certification
IoT Component Security Assurance (ICSA) is a security certification program developed by ISASecure for IIoT devices and IIoT gateways which is based upon the ISA/IEC 62443 standards. This certification provides recognition of product security characteristics and capabilities, as well as providing an independent industry stamp of approval like a SIL (Safety Integrity Level) Certification (IEC 61508). ICSA has requirements like creating internal zones using compartmentalization technologies, controlling application of software updates, securing remote management, device authentication strength, and component resilience to cloud services or the cloud interface. In addition, an ongoing security maintenance audit is required to maintain certification.
Conclusion
IIoT is disruptive technology that is growing rapidly, but without proper security may not reach full potential. To effectively harness the power of IIoT, stakeholders must improve their industrial cybersecurity posture, and device identity management is a key consideration to secure IIoT devices where the process must be protected for both authenticating devices and authorizing access based on permissions. However, securing IIoT infrastructures calls for a much broader security strategy since critical systems are now becoming desirable targets for cyber attackers.




