The integration of IT and OT is a well-established trend, driven by the business benefits that typically come with richer real-time information sharing, analysis, and response. While the cybersecurity concerns of this integration are numerous and potentially significant, the horse has left the barn, so to speak, and cybersecurity teams need to respond strategically across infrastructure domains.
This integration of technology is driving an associated integration of IT and OT cybersecurity teams and a consolidation of responsibility for strategy. An interesting byproduct of that consolidation is the application of best practice IT cybersecurity models in OT environments. Two that have been gaining traction over the last several years are Forrester’s Zero Trust Model and Gartner’s Continuous Adaptive Risk and Trust Assessment (CARTA).
Zero Trust in OT Networks
Zero Trust is the older of the two strategies and currently has greater market awareness, but there is actually a sizable amount of overlap between the approaches, which demonstrates a growing consensus on best practice approaches to securing IT and OT infrastructure and data. As the name implies, Zero Trust is based on the simple premise that there is no such thing as a trusted source. This means that cybersecurity teams need to assume that there are attackers present both inside and outside of their networks, and therefore treat all traffic as suspect. This, in turn, suggests that no communications should be allowed until each party is properly authenticated and authorized.
The Zero Trust concept has expanded over the years from its early focus chiefly on micro-segmentation of networks. Network segmentation, of course, isn’t new. Security teams have used firewalls, access control lists (ACL), and virtual local area networks (VLAN) for network segmentation for years. Micro-segmentation differs in several ways. While traditional segmentation was chiefly concerned with controlling north/south traffic (e.g., in and out of a data center), micro-segmentation is chiefly concerned with segmenting traffic moving east/west (e.g., between applications in a data center).
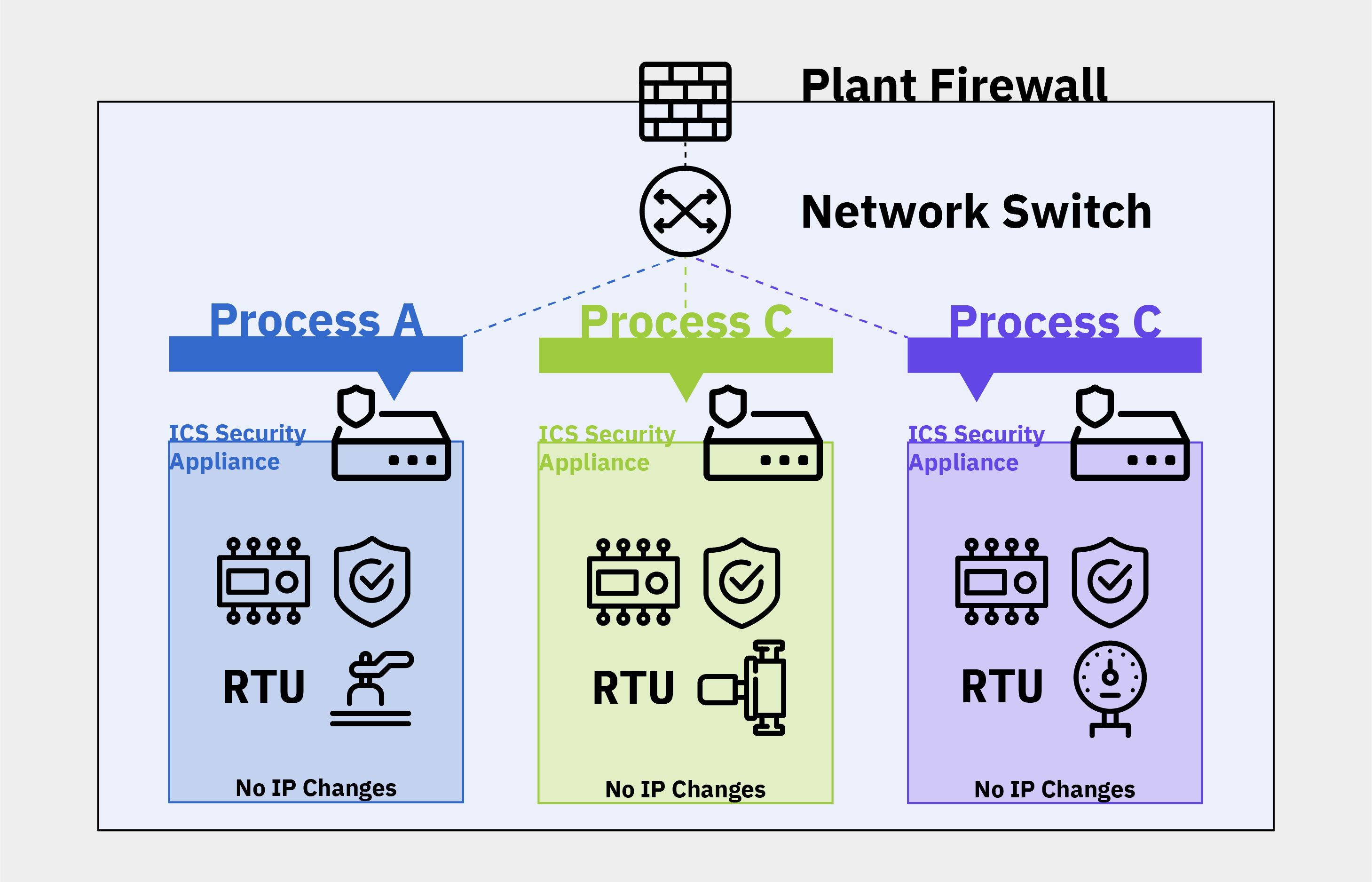
One example of micro-segmentation or process segmentation in OT environments
The term Software Defined Perimeter was introduced in 2016 in a Gartner research paper, and its utility in enabling Zero Trust was recognized. The Cloud Security Alliance (CSA) recently released a whitepaper titled Software-Defined Perimeter (SDP) and Zero Trust, which makes the case that Software Defined Perimeter is, in fact, the most advanced implementation of a Zero Trust strategy. SDP can also be used effectively to enable micro-segmentation.
The CSA calls out the following three requirements for implementing SDP:
- Separating the control plane where trust is established from the data plane where actual data is transferred
- Hiding the infrastructure (e.g., blackening the servers) using a dynamic deny-all firewall (not deny-all, allow exceptions)—the point where all unauthorized packets are dropped for logging and analyzing traffic
- Using single packet authorization to authenticate and authorize users and validate devices for access to protected services—least privilege is implicit in this protocol
OT cybersecurity teams need to cloak all assets by providing no public IP addresses or open ports willing to accept connections. Authentication and authorization need to be completed prior to network connection acceptance, and access controls should take into consideration the current security posture of devices before granting access. After approval, connections should be monitored, analyzed, and audited.
This Zero Trust/SDP model requires the adoption of a least privilege access strategy that assigns access permissions to users, applications, and data based on specific and defined need. Secure access is enforced regardless of where (e.g., inside or outside the LAN) access is requested, and access controls are fine-grained and revocable. It is also important that all access control activity is logged and audited with the ability to generate alerts automatically.
Continuous Adaptive Risk and Trust Assessment (CARTA) in OT Networks
The Continuous Adaptive Risk and Trust Assessment (CARTA) strategy takes an even broader view of security than Zero Trust or SDN. But CARTA overlaps with Zero Trust in several important ways. Gartner sees Zero Trust as a necessary but not sufficient step in achieving CARTA. As described by Gartner, the Continuous Adaptive Risk and Trust Assessment (CARTA) Imperatives are as follows:
Imperative No. 1: Deploy Context-Aware, Adaptive, and Programmable Security Platforms
Imperative No. 2: Continuously Discover, Monitor, Assess, and Prioritize Risk—Proactively and Reactively
Imperative No. 3: Perform Risk and Trust Assessments Early in Digital Business Initiatives
Imperative No. 4: Instrument Infrastructure for Comprehensive, Full Stack Risk Visibility, Including Sensitive Data Handling
Imperative No. 5: Use Analytics, AI, Automation, and Orchestration to Speed the Time to Detect and Respond, and to Scale Limited Resources
Imperative No. 6: Architect Security as an Integrated, Adaptive Programmable System, Not in Silos
Imperative No. 7: Put Continuous Data-Driven Risk Decision Making and Risk Ownership Into Business Units and Product Owners
Several of these imperatives clearly overlap with Zero Trust, particularly Imperative No. 3. In practice, both strategies demand:
- 100% endpoint discovery, visibility, and control
- Posture assessment and remediation or blocking of physical and virtual devices
- Ability to manage agentless IoT devices and cyber-physical OT systems
- Micro-segmentation to limit lateral movement through networks and contain breaches
- Continuous monitoring, assessment, and remediation of operational and cybersecurity risk
Getting Started: Implementing OT Micro-Segmentation as a First Step
OT cybersecurity teams should embrace the maturing Zero Trust strategy and focus on enabling a Software Defined Perimeter as a means of achieving that goal. Fully implementing SDP, however, should be viewed as a long-term objective. Micro-segmentation can be effectively achieved with more traditional technologies and should always be considered a best practice in implementing a Zero Trust strategy.
That said, the fine-grained access controls that are supported with Software Defined Perimeter will enable the use cases that are driving continued IT and OT integration, such as per-workload access controls in virtualized data centers and cloud applications. SDP can be viewed as the first steps in a broader embrace of a CARTA strategy, but they are significant undertakings in their own right.
A version of this post also appears on the Mission Secure blog. It is republished here with the permission of its author.
Interested in reading more articles like this? Subscribe to the ISAGCA blog and receive weekly emails with links to the latest thought leadership, tips, research, and other insights from automation cybersecurity leaders.



