In light of EO 14028 of May 12, 2021, ISAGCA was given the opportunity by the National Institute of Standards and Technology (NIST) to respond to the Workshop and Call for Position Papers on Standards and Guidelines to Enhance Software Supply Chain Security. ISA Managing Director Andre Ristaino submitted the following comments on behalf of ISAGCA member companies.
The following has been abridged from its original version:
“ISAGCA Member companies and thought leaders have a long history of adopting a standards-based approach for securing automation products and operating sites based on the ISA/IEC 62443 series of international cybersecurity standards. The scope of ISA/IEC 62443 standards applies to critical software in all phases of the automation solution lifecycle.
Product suppliers have been developing automation products using ISA/IEC 62443 security lifecycle practices in their development processes since 2010. Companies are having their development processes and products independently audited/certified to be conformant with ISA/IEC 62443 via accredited certification bodies…End users (asset owner/operators) are establishing cybersecurity programs at operating sites based upon ISA/IEC 62443, including their critical software.
The internationally recognized ISA/IEC 62443 standards have been adopted in the USA and throughout the globe. This is important since most product suppliers (includes critical software) have global customers. Further, many end-user companies operate internationally. ISA/IEC 62443 provides a common vocabulary for managing cybersecurity capabilities. A globally accepted set of standards reduces barriers to trade where country-specific product certifications are mutually recognized. It also provides end-users the basis for establishing companywide cybersecurity practices useful in all geographies.
ISAGCA asks that you consider these additions to the Executive Order:
- Reference these standards when defining “Critical Software”: EO Section 4(g).
- ISA/IEC 62443-3-3-SR.5.2RE(2)/RE(3); ISA/IEC 62443-4-2-CR.2.10/CR.7.1) to define commands and essential functions including parameters and associated data that must be properly protected either by built-in technical capabilities (ISA/IEC 62443-4-2), integrated system capabilities (ISA/IEC 62443-3-3) and/or procedural/organizational capabilities(ISA/IEC 62443-4-1; ISA/IEC 62443-2-4 and ISA/IEC 62443-2-1).
- ISA/IEC 62443-2-4 standard defines best practices for OT Service Providers with a set of security capabilities that an organization needs to have while designing a secure automation solution. That includes the associated, hardware, software, and data.
- ISA/IEC 62443-2-4-SP.03.01BR provides Rationale to ISA/IEC 62443-3-2 including capability to translate a business, production and ultimately safety risk into technical and procedural capabilities that a system needs to encompass to become feasible
- ISA/IEC 62443-2-4-SP.03.09BR/10BR) including its safeguarding requirements needed to perform the risk translation includes the capacity to identify and manage security vulnerabilities and associated threats for all the associated components of the automation solution and its authorized data storage points, data flows and control actions by design
- Reference ISA/IEC 62443 4-1 Product Security Development Life-Cycle Requirements as a standard to secure software development lifecycle for Operational Technologies. EO Section 4(e) which describes component or system development lifecycle requirements related to cyber security for those components or systems intended for use in an OT environment and provides guidance on how to meet the requirements described for each element. When a Product Supplier is using an ISA/IEC 62443-4-1 compliant process, enables a Service Provider to follow the ISA/IEC 62443-2-4 compliant practices to integrate, configure, validate, commission, and maintain an intended security posture by design.
- Reference ISA/IEC 62443 4-2 Technical Security Requirements for Automation Components as a standard to secure software development lifecycle for Operational Technologies components. EO Section 4(e)
- Reference ISA/IEC 62443 3-3 System Security Requirements and Security Levels as a standard to define security measures that shall be applied to the federal government’s use of critical software. E.O. Section 4(I)
- Reference ISA/IEC 62443 4-1 Product Security Development Life-Cycle Requirements (Section 9) to define the minimum requirements for testing software source code. See EO Sections 4(e)(iv, v) and 4(r).
- Reference ISA/IEC 62443-4-1-SM-9 Security Requirements for externally provided components requires software development organizations to have a process to identify and manage security risks of all externally provided components used within the product. An SBOM implementation can be utilized as a method satisfy this requirement. The rationale of that requirement provides the guidance for compliance, referring to the Defense in Depth strategy, identifying all components as well as their security context, rigor applied to the component implementation, verification/validation, notifications, etc.”
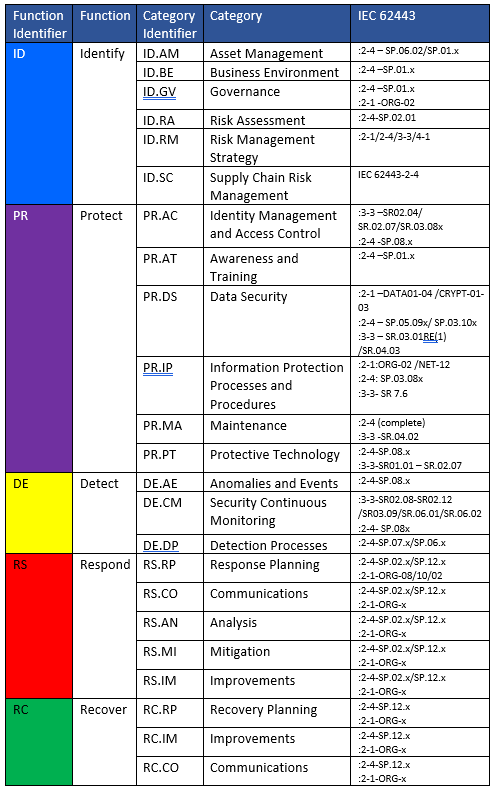
ISAGCA also provided the following table, which shows where the ISA/IEC 62443 standards align with NIST’s Cybersecurity Framework (CSF) requirements:
To view the full response, click here.
Editor's Note: On May 27th, 2021, in response to recent cyber attacks, the Department of Homeland Security’s Transportation Security Administration (TSA) announced a Security Directive that will enable the Department to better identify, protect against, and respond to threats to critical companies in the pipeline sector.
This Directive will require critical pipeline owners and operators to report confirmed and potential cybersecurity incidents to the DHS Cybersecurity and Infrastructure Security Agency (CISA) and to designate a Cybersecurity Coordinator, to be available 24 hours a day, seven days a week. It will also require critical pipeline owners and operators to review their current practices as well as to identify any gaps and related remediation measures to address cyber-related risks and report the results to TSA and CISA within 30 days. To read the full report, click here.
ISAGCA's position has always been that any regulatory requirements or specifications should include ISA/IEC 62443, as it is widely adopted by all kinds of industry sectors and is actionable, testable, and certifiable.




