A version of this blog originally appeared on Cisco
Implementing security inside the industrial network can be a daunting task. Security directives such as the Cybersecurity and Infrastructure Security Agency (CISA)’s Shields Up have caused more industrial organizations to assess their network posture and seek guidance to improve the protections of critical resources for business continuity. Upon seeking this guidance, many are left confused with terms such as Zero Trust and Microsegmentation, resulting in more questions and no route to action.
Security can, and should, be simple. Whether you follow guidance from ISA/IEC 62443—the National Institute of Standards and Technology (NIST)—or have implemented the Purdue model, the core security principle is to divide the network into multiple zones and create policy for the communication that crosses zone boundaries.
Defining Secured Zones
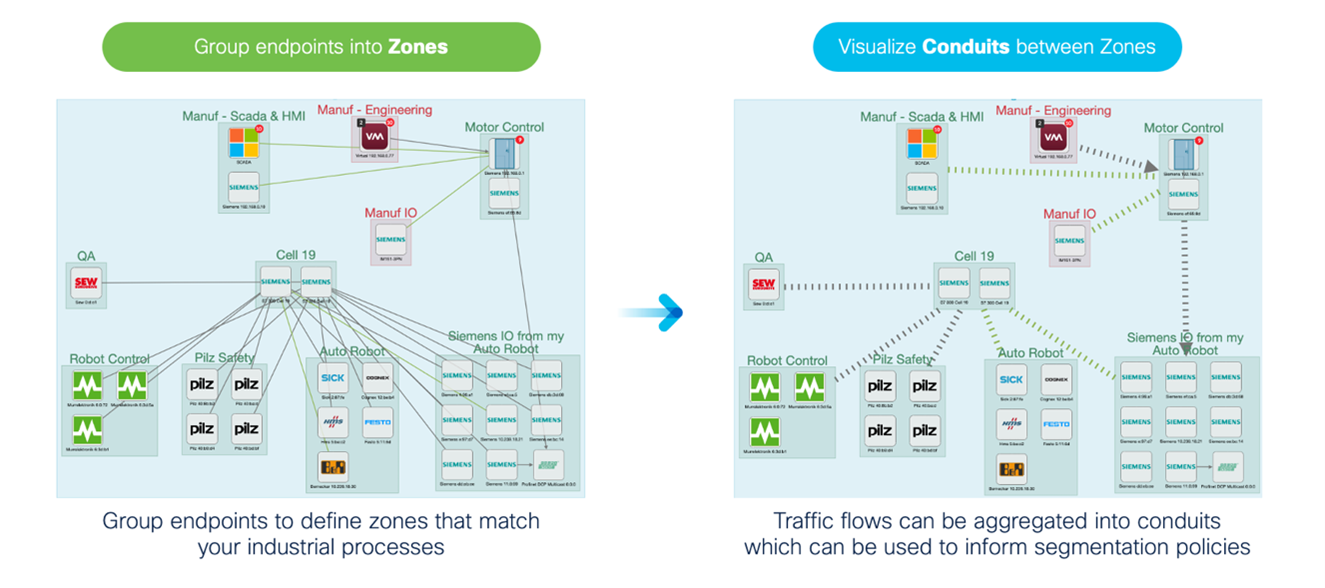
Let’s take the ISA/IEC 62443 definition of zones and conduits. A zone, according to the standard, is a collection of physically and functionally united assets that have similar security requirements. In a manufacturing facility, this could be a single production line. A conduit is described as the communication between zones. The conduit is the communication channel in which security policy should be applied.
Defining the zones and knowing which policy to assign to the conduits is what makes security perceived as difficult. However, segmentation should not be viewed as a single standalone task. Effective segmentation is comprised of two key pillars: Visibility and control.
ICS Visibility Informs OT Segmentation
Visibility into industrial control system (ICS) operations gives us an inventory of all assets that exist on the network, along with their communication patterns. This enables us to visualize the processes in our networks and answer the question: What are the zones on my network? Using a product such as Cisco Cyber Vision, an ICS visibility tool that is embedded into the network infrastructure, operators can identify assets that belong to a process and assign them to a group for easier visualization. Rather than focusing attention on every flow, from every asset, communication can be visualized in the conduits between the zones, providing a blueprint of the policy that must be defined.
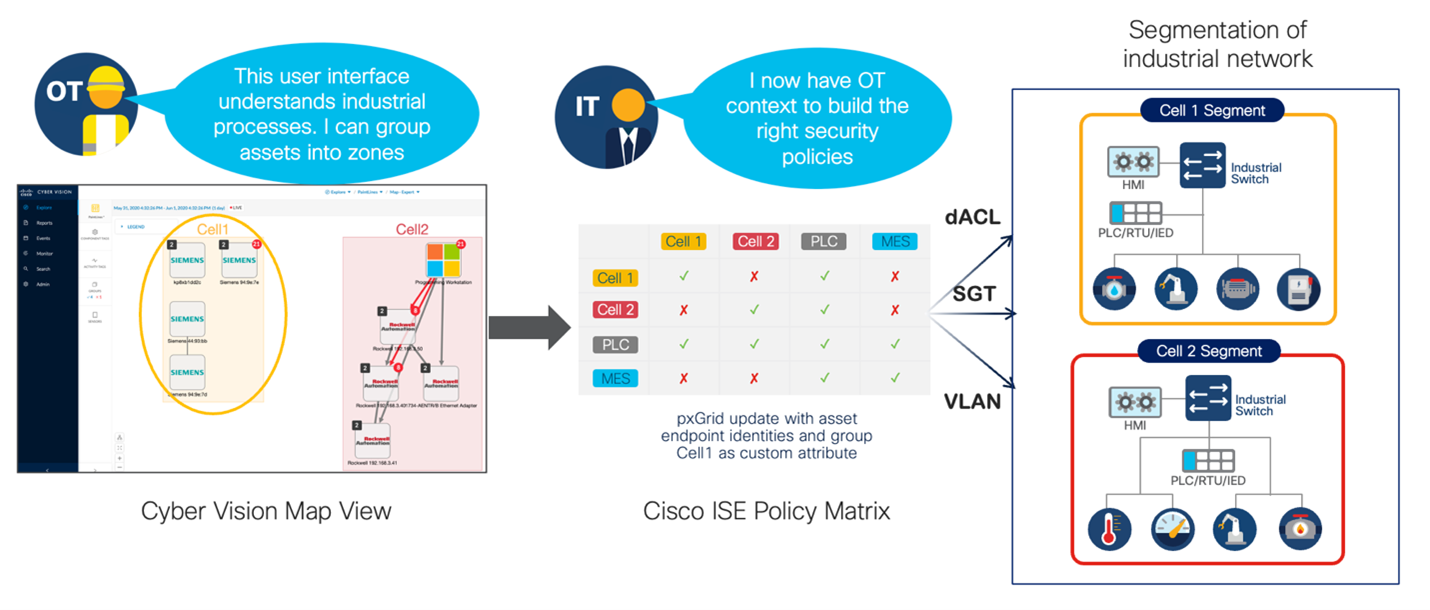
 As for the enforcement of these traffic patterns, that too can be embedded into the network infrastructure using a Cisco technology called TrustSec. Cisco TrustSec manages access control policies across switches using a security group matrix. As traffic enters and leaves their network segment, rather than enforcing traffic using internet protocol (IP) information, Cisco TrustSec uses a Security Group Tag (SGT) embedded in the MAC layer of the network traffic to determine policy. This Cisco Identity Services Engine (ISE) allows SGTs to be assigned to zones and the matrix can be used to control the communication across the conduits.
As for the enforcement of these traffic patterns, that too can be embedded into the network infrastructure using a Cisco technology called TrustSec. Cisco TrustSec manages access control policies across switches using a security group matrix. As traffic enters and leaves their network segment, rather than enforcing traffic using internet protocol (IP) information, Cisco TrustSec uses a Security Group Tag (SGT) embedded in the MAC layer of the network traffic to determine policy. This Cisco Identity Services Engine (ISE) allows SGTs to be assigned to zones and the matrix can be used to control the communication across the conduits.
With integrations, Cyber Vision shares its grouping information with Cisco ISE so operations managers can create and manage assets groups in their operational technology (OT) visibility tool, so information technology (IT) can easily create the proper control rules between those zones in ISE.
 In a recent webinar, I went into more details diving into the ISA/IEC 62443 zones and conduits model and showing how to use Cisco ISE and Cyber Vision to enforce OT Microsegmentation. Watch the replay by registering here.
In a recent webinar, I went into more details diving into the ISA/IEC 62443 zones and conduits model and showing how to use Cisco ISE and Cyber Vision to enforce OT Microsegmentation. Watch the replay by registering here.
Until then, have a look at Cisco's ISA/IEC 62443-3-3 white paper and subscribe to the Industrial Security Newsletter.




