Modern keyboard, video, and mouse (KVM) systems are not just a way to improve efficiency and flexibility into an operation. Sophisticated KVM technology also provides an additional step toward protecting against cyberattacks. KVM systems build the backbone of information technology (IT) and operational technology (OT) supported processes in organizations. By separating man from machine, they provide an optimal basis for seamless interconnection of all used systems and seamless IT integration in industrial process automation.
Simply put, KVM removes computers from the workplace and stores them in a dedicated technical area free from the noise, clutter, heat, and dust of a production floor or control room (along with latency-free remote access). Further, it allows an individual user to operate several processes simultaneously. Each workstation can consist of multiple screens, and each screen can show individual computer sources that operators can survey and operate all at one time. KVM allows the right system availability at the right time. The user can easily switch between computers and handle complex consoles with many screens, but with just a single keyboard and mouse.
KVM Helps Mitigate Cybersecurity Risks
Cybersecurity is an important aspect that KVM solutions allow to make installations more secure. Removing the computer from the desk is a core strategy for protecting its access. For starters, you cannot directly connect a USB drive or plug in a USB drive to a computer anymore. Data shows that most cyberattacks originate internally—either by human error or on purpose—as opposed to outside factors.
Externally, modern KVM systems allow an organization to achieve “network separation.” With different security classifications of the networks (dedicated networks where all the critical processes run, and a separate network that may even have access to the public internet, which would make it more at-risk of an external attack), the risk of cyberattacks can be minimized. KVM systems provide the basis for flexible system access and help to harmonize computer technology across systems.
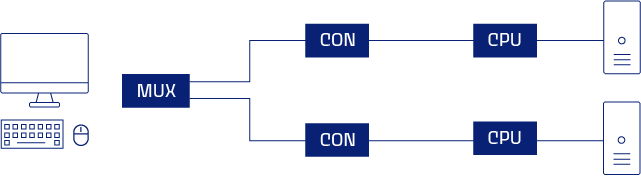 Ensuring cybersecurity with separate computers connected to different networks, operated from a single user interface.
Ensuring cybersecurity with separate computers connected to different networks, operated from a single user interface.
With KVM, users only access the computer interfaces, not the computers themselves. Several systems are accessible at the same time, but without a data connection between the systems. Organizations can separate critical internal applications in the data flow from external applications like web surfing or external video conferencing. For example, they can keep the critical processes on the internal network and everything that is connected to the outside world can be kept separate.
Ensuring Security Through Redundancies
KVM systems offer numerous options for creating redundancies for mission-critical applications. Depending on the complexity and requirements of individual applications, the respective redundancy concept can be either rather simple or quite sophisticated and complex. Redundancies back up either only the KVM system, the computer side, the console side, or the entire application. For smaller applications, redundancy can already be ensured by using a local switch.




