A Security Operations Center (SOC) functions as a team of skilled people operating with defined processes and supported by integrated security intelligence technologies. The SOC specifically focuses on cyber threat, monitoring, forensic investigation, and incident management and reporting under the umbrella of an overall security operations environment and clear executive support. Without such an umbrella, a SOC is ineffective, and its value is not realized.
The biggest question businesses then ask is, how do we future proof our SOC? In recent years, SOCs have taken a drastic turn and experienced immense fatigue by alerts, false positives, burnouts, and a constantly changing threat landscape. On top of this, maintaining security exercising by keeping a low impact on the operations of business is a gargantuan task even for the most skilled SOCs. Additionally, in many businesses, SOCs do not have an appropriate authority within the organization (i.e., a SOC team is not permitted to take a quick action without a signoff; how can they promptly respond to an incident and stop an ongoing intrusion?). An additional overlooked aspect is the struggle to retain staff. A SOC team and threat hunters need to have bleeding edge training, sufficient time off, and focus on their self-improvement because their mission is to match (and ideally exceed) the skills of their adversaries.
 In many organizations, the increased volume of alerts is such a huge undertaking that the SOC is overburdened with several tasks and the limitation on the execution phase holds off many critical events, which leads to response delays and burnout on the job. Traditional SOCs are no longer a viable and smooth security operation.
In many organizations, the increased volume of alerts is such a huge undertaking that the SOC is overburdened with several tasks and the limitation on the execution phase holds off many critical events, which leads to response delays and burnout on the job. Traditional SOCs are no longer a viable and smooth security operation.
The Challenge
A SOC is vital to any organization’s ability to sustain operations, and this is where operational technology (OT) kicks in. The convergence of informational technology (IT) and OT processes and governance has highlighted the need to be much more scalable and robust when it comes to applying SOC principles in various OT environments.
According to Gartner, organizations with both IT and OT struggle with the coexistence of two separate security and risk management functions. This leads to a dispersed view on the overall operational risk the organization is facing. In a continuously evolving threat landscape, a single established security and risk management function is better positioned to address these threats across both IT and OT. A single leader of this function can also be held accountable for the organization’s overall digital risk. As an added benefit, scarce security resources can now be deployed to address both IT and OT.
An IT/OT SOC is a forward-thinking way to address and mitigate cyber risks organization-wide. A combined structure taps into the individual strengths of IT and OT team members, ultimately creating a faster, comprehensive, and more cost-effective approach to digital risk management. Still, with growing threat of cyberattacks with such a large threat surface, it can become an impossible task to keep up with SOC principles on both the IT and OT landscape and respond in time.
An effective cybersecurity strategy requires an investment in an array of security solutions designed to address and mitigate a wide variety of potential threats across the space. With technology advancement, manning a full-service SOC in-house makes it much more challenging.
SOC as a Service (SOCaaS)
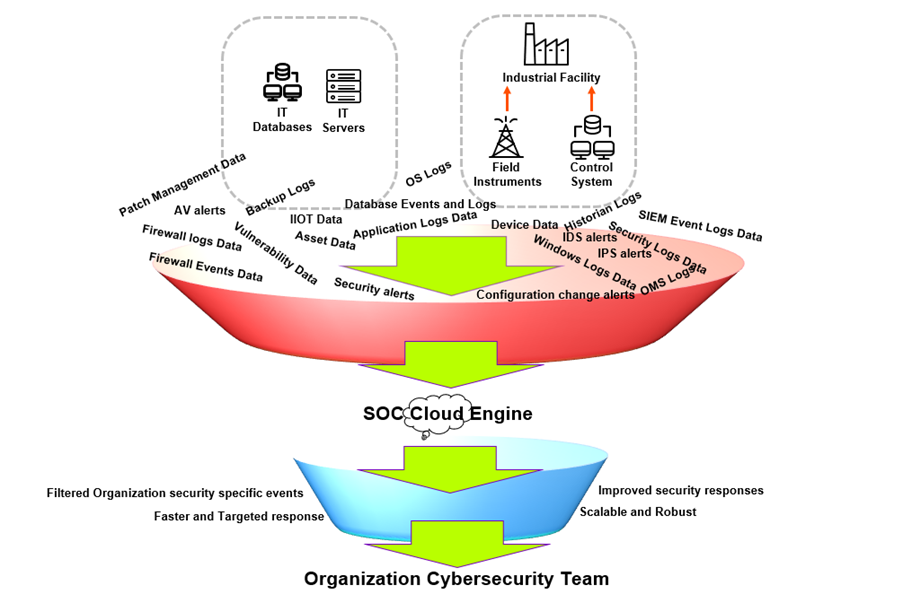 SOC plays an essential role as a command-and-control hub for the organization's cybersecurity. The service will not only bring more accuracy, but with smart automation techniques, SOC events will get filtered at a much faster rate than traditional SOCs. With a SOC cloud engine, providers can connect its database with a wider cloud detection base, and this will not only enable the wider threat pool search, but also help the SOC security experts focus more on high-risk alerts.
SOC plays an essential role as a command-and-control hub for the organization's cybersecurity. The service will not only bring more accuracy, but with smart automation techniques, SOC events will get filtered at a much faster rate than traditional SOCs. With a SOC cloud engine, providers can connect its database with a wider cloud detection base, and this will not only enable the wider threat pool search, but also help the SOC security experts focus more on high-risk alerts.
This model can also leverage technology like artificial intelligence (AI). AI-powered autonomous platforms will be highly efficient in attack mitigation and forensic investigation. AI can also be used in proactive threat hunting, which can bring a whole new dimension to the SOC.
SOCaaS is a wide-open market, and we do not have a global player yet. Organizations need this now, and it will be a matter of time before someone steps in first that will take over most of the market. SOC is no longer just a security control hub, its more and more active threat hunting.
References
IBM, “Strategy Considerations for Building a Security operations Centre,” 2013.
Checkpoint- SOC as a Service SOC-as-a-Service - Check Point Software 2022.




