 Science has come a long way since Aristotle’s theory of air, water, fire, and earth. Just like Aristotle’s theory, I consider the four key security elements as design, technology, people, and process. I like to call it the Security Tetrahedron. With advancements in our digital era the critical objective is to protect the information and especially the processing technology and infrastructure of the information.
Science has come a long way since Aristotle’s theory of air, water, fire, and earth. Just like Aristotle’s theory, I consider the four key security elements as design, technology, people, and process. I like to call it the Security Tetrahedron. With advancements in our digital era the critical objective is to protect the information and especially the processing technology and infrastructure of the information.
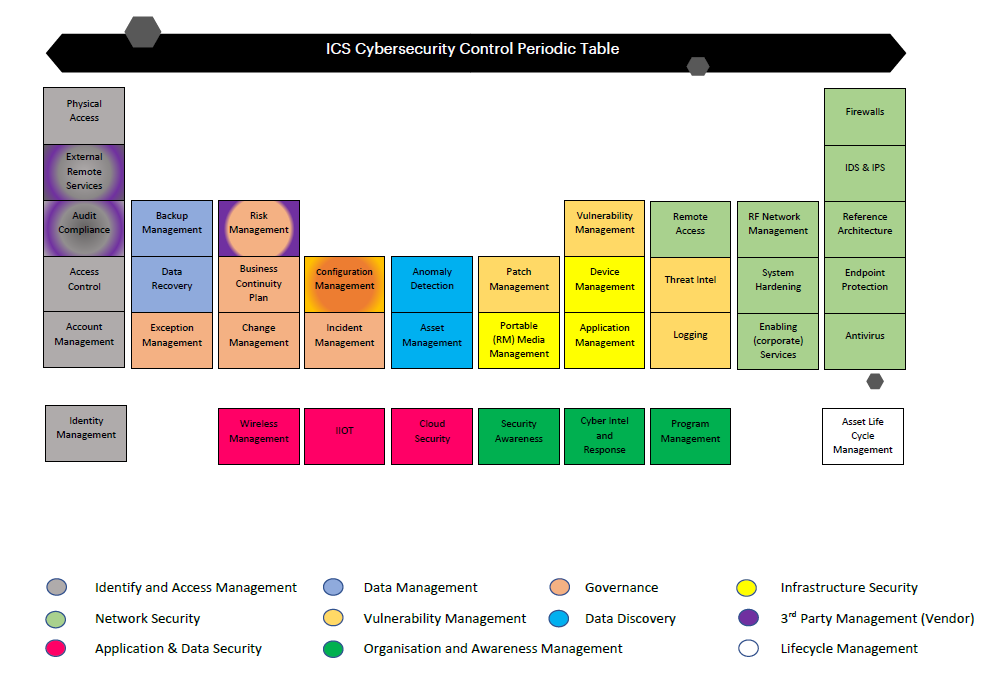
This industrial control systems (ICS) periodic table depicts the chemistry of all the control elements which enables the security around the operational technology (OT) estate for any organization. Industrial OT refers to the hardware and software which are used to manage the controls systems for industrial processes. ICS, such as supervisory control and data acquisition (SCADA) are used across industries.
Computing environments are rapidly transforming to deliver business outcomes for modern consumers in a modern world. Network perimeters continue to erode to enable this transformation and include mobile devices, cloud applications and platforms, OT such as sensors and controls, and industrial internet of things (IIOT) devices. Cybersecurity has become an encompassing term, with a variety of complex technology across wider estates.
Effective integration of cybersecurity into the operation of OT requires defining and executing a comprehensive program that addresses all aspects of security and all the modules that are related to security. This includes defining the objectives and scope of the program, establishing a distributed functional team that understands OT and security, defining policies and procedures, identifying the cyber risk management capabilities that include people, process, and technology, as well as identifying day-to-day operations of event monitoring and auditing for compliance and improvement.
With new asset being installed in current OT and information technology (IT), it is imperative to take the time to address security throughout the lifecycle, including procurement, architecture, installation, maintenance, and decommissioning. Deploying systems to the field based on the assumption that these systems will be secured later introduces significant risk to the systems and the organization. If there isn’t sufficient time and resources to secure the system properly before deployment, it is unlikely that security will be addressed later. Since new OT assets are designed and deployed less frequently than IT systems on a complete landscape, it is much more common to improve, expand, or update an existing OT system than to design a new one.
Risk Landscape Without Proper Security Controls
In the traditional IT world, risk involves threats that would undermine the confidentiality, integrity, and availability of data and systems. The impact is mainly financial, such as the cases of extortion (i.e., CryptoLocker), bank fraud, or denial of service (DoS) attacks distributed on web servers used by e-commerce sites.
ICS drives the physical world where operational technologies are used. The risk in ICS environments involves threats that would undermine the operational safety (i.e., physical security of goods, people, and environmental impacts) and the availability or even the physical integrity of the production tool. Theft of critical industrial data is also feared.
The potential impact of a cybersecurity event could be severe—it could impact the organization’s mission and objectives, the environment, regulatory compliance, and even human safety. The impacts are economic but also social; the civil and criminal liability of leaders is also engaged. ICS have never been designed to deal with cybersecurity threats. They are created with the objective of ensuring operational safety and the continuity of operations, and they often do not consider the possibility that a motivated and malicious intruder could reach their digital interfaces. Therefore, security should be in the heart of the overall organization landscape.
Reference: NIST SP800-82




