The practice of steganography—concealing messages or information within text or data—is far from new. During the Cold War, newspapers and radio shows were regularly used to send coded messages and instructions to spies behind enemy lines. The modern day version, however, is used not to convey instructions to humans, but as a means of weaponizing seemingly benign files with malware.
In the context of cyberattacks, steganography is often (but not always) used in conjunction with spear-phishing attacks. The attacker sends an email or other type of message, seemingly from a trustworthy contact, with an intriguing image or common computer file (e.g., a spreadsheet or Word document), often accompanied by a call to action (“I couldn’t stop laughing!” or “You really should read this!”) Then, clicking on the image or opening the file triggers an executable containing malicious content.
Steganography enables the attackers to evade some security tools, including network traffic scanners. In the case of images, the malicious data (e.g., PowerShell script) is encoded within specific pixels in publicly hosted images (which makes detection by common network traffic scanners very difficult). In other cases, downloading a file, (e.g., MS Word or Excel file), will prompt the user to allow active content (macros) on the document, which, in turn, will activate a malicious payload.
The nefarious payload itself, if gone undetected, can wreak havoc on both sides of the IT/OT divide: it can change SCADA systems’ operating values or change logics in networked device; on the IT side the malware can open a C&C channel for exfiltrating sensitive corporate data.
According to Kaspersky, up to 50% of steganography attacks targeted industrial organizations. Some of the attacks took advantage of the network interconnectivity between the organization and its smaller vendors/suppliers, which may have weaker protections or email safety policies. By harvesting vendors’ employees’ credentials, attackers are able to remotely wreak havoc on the larger organization’s network.
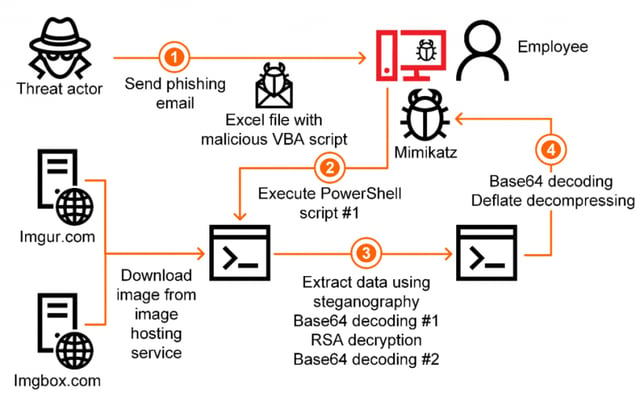 Workflow of steganography-based cyberattacks (Source: Kaspersky)
Workflow of steganography-based cyberattacks (Source: Kaspersky)
This newly-discovered campaign against hardware and software suppliers to industrial enterprises again sheds light on the cyber risk originating from enterprises’ supply chains and partners.
Many sources speculate that these attacks were state-sponsored.
Such attacks may serve a number of purposes:
- First and foremost, economic espionage
- Secondly, they could be used to get deep insights into software/hardware design and find zero-day vulnerabilities that can be then exploited in attacks against enterprises that use these products
- Thirdly, one of major and more common techniques for highly-skilled hackers is to embed a malware or a backdoor in this type of product for later use at their deployments (as was the case in CCleaner and NotPetya)
- Finally, the stolen suppliers’ credentials can be used for initial access into to their customers’ networks during periodic maintenance and service (like in the famous “Cloud Hopper” campaign)
Prevention and Mitigation
Preventing steganography-based cyberattacks requires both making sure that employees don’t activate the hidden malware (e.g., by opening a photo or allowing macros in MS Office documents), and, as a second line of defense, had an employee activated the malware, detecting the network activity triggered by the malware.
- Network segmentation and segregation: one of the key structural changes all industrial organization should implement is maintaining separation between operational and IT networks using firewalls and DMZs
- Human/social engineering: this activity involves employee training on what steganography and phishing attacks are, what to look for in illegitimate emails, and procedures for reporting to IT department; some organizations actually hold phishing-preventing exercises for senior/sensitive position-holders, and even penalize employees for not following email safety guidelines
- Detection by an IDS: while files containing hidden malware can’t always be detected prior to human activation, Intrusion Detection Systems (IDSs) such as Radiflow’s iSID are able to detect minute changes in network behavior that indicate the triggering and the propagation of malware, such as connecting to a previously unused hosting server, opening new external connections, and/or unusual data traffic patterns
Conclusion
The slew of attacks described above yet again demonstrates that it is imperative that stakeholders in industrial enterprise cybersecurity (CISO, OT security manager, Chief Risk officer, and so on) manage their organization’s cyber risk properly, validate the security posture of suppliers, monitor third-party network access, and deploy threat detection tools at the production lines to alert on possible exploits.
There’s no magic bullet that can prevent steganography-based cyberattacks prior to activation of the hidden malware contained in the carrier medium. An effective security plan should involve segregating between OT and IT networks (using firewalls and DMZs), raising awareness and educating employees, and installing an IDS that is able to instantly detect network behavior patterns indicating a malware attack.
This post originally appeared on the Radiflow blog. It is republished here with the permission of its author.
Interested in reading more articles like this? Subscribe to the ISAGCA blog and receive weekly emails with links to the latest thought leadership, tips, research, and other insights from automation cybersecurity leaders.



