ISA/IEC 62443 provides a powerful tool to reduce the risk of financial, reputational, human, and environmental impact from cyber-attacks on Industrial Automation and Control Systems (IACS). However, since it is a “horizontal standard”, 62443 is meant to address a wide range of industries, and any specific company is likely to find that while most of the standard applies to their IACS, parts of it may not. For example, some “normative requirements” that are appropriate for an interstate pipeline, may not be relevant to a chemical plant or a discrete manufacturing facility. There are also obvious differences between a large-scale corporation with many sites and thousands of employees, and a small company with a few dozen staff.
It is therefore recommended that each company establishes their own Industrial Automation and Control Systems (IACS) Cybersecurity Program to manage these cybersecurity risks. ISA/IEC 62443 2-1 provides guidance on how to establish a Security Program for IACS asset owners. This process might look like the following.
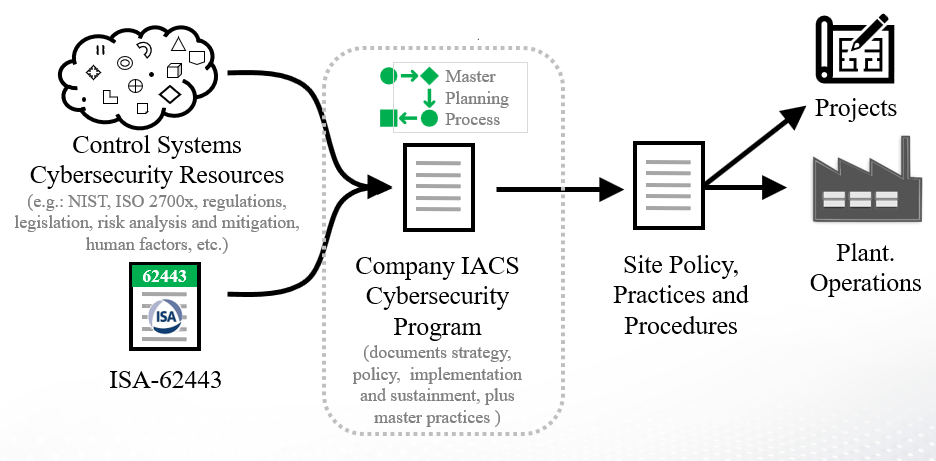 Figure 1 - IACS Cybersecurity Program Workflow
Figure 1 - IACS Cybersecurity Program Workflow
This white paper is intended to address the needs of Owner/Operators of industrial facilities. It will discuss the following:
- What is an IACS Cybersecurity Program?
- Preparing an IACS Cybersecurity Program
- How does an IACS Cybersecurity program relate to IT Cybersecurity?
- Costs and Benefits of an IACS Cybersecurity Program
- What to do next
In the coming months, ISA plan to publish additional white papers intended for IACS vendors, suppliers of IACS products and services, Integration/engineering services, and possibly other major stakeholders such as insurers and regulators.
What is an IACS Cybersecurity Program?
An IACS Cybersecurity Program (yellow) defines the company’s IACS security policies, practices, and procedures associated with the operation and design of the company’s industrial facilities.
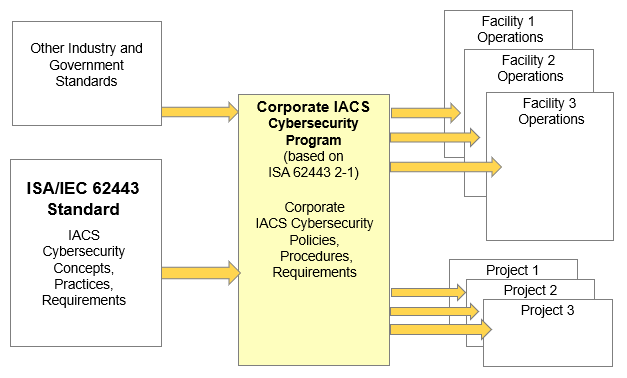 Figure 2 – IACS Cybersecurity Program Concept
Figure 2 – IACS Cybersecurity Program Concept
As this diagram indicates, the ISA/IEC 62443 standard provides Concepts, Practices, and Requirements that may be included in a corporate IACS cybersecurity program.
Note that a Corporate IACS Cybersecurity program is a necessary first step, however, the Policies, Procedures and Requirements defined in this program, must then be implemented within existing Corporate and Facility procedures if they are to be effective. This implementation should be undertaken as one or more projects, with stated schedules, scopes, and budgets; and must include training and management of change to address human and organizational aspects.
At present, the 62443 standard identifies over 500 separate requirements that may be necessary for a given company’s facilities. It is impractical to search through ISA/IEC 62443 to determine what is necessary for a given project or operating facility. A key objective of the IACS Cybersecurity Program is therefore to establish approved requirements that may then be incorporated in project or facility standards and procedures.
A corporate IACS cybersecurity program must select which ISA 62443 requirements to include for:
- A company’s Existing Facilities
- New company projects that involve IACS
A new company project for IACS can include most of the ISA 62443 requirements that address
the design and operation of the asset. Existing Facilities will not be redesigned to meet all those
requirements because that effort would be cost prohibitive. Therefore, many design requirements will have to be introduced over a longer period of time as major changes occur to Existing Facilities. These Existing Facilities can quickly address the program and operational requirements in ISA 62443.
As shown in Figure 2, requirements and recommendations from other industry, national, and international standards, may also be considered for inclusion in the company’s IACS Cybersecurity Program. Examples of these might include:
- ISA standards such as:
- ISA84 (safety instrumented systems),
- ISA95 (enterprise integration),
- ISA100 (Industrial wireless networks), and
- ISA108 (intelligent device configuration)
Note: Since ISA standards are internally “harmonized”, use of these together with ISA/IEC 62443 may save considerable time and effort for the Owner/Operator.
- Additional cybersecurity standards and guidelines from NIST, NAMUR, ISO, IEC, and others
- Standards and guidelines for human factors, risk analysis and risk mitigation.
- Human Factors:
- ISO 6385 Ergonomic principles in the design of work systems
- ISO 26800 Ergonomics – General approach
- API Human Factors 2005 & 2006
- IEC 62879 Human factors and functional safety
- Risk Analysis/Mitigation:
- ISO 27xxx series
- NIST 800-30 Guide for Conducting Risk Assessments
- NIST CSF
- Human Factors:
Many of the above have been aligned with ISA/IEC 62443, including cross-reference documents and other whitepapers.
Examples of government standards include regulations and legislation at national, state, and local levels, like NERC-CIP. These must also be considered when creating the Corporate IACS Cybersecurity Program.
ISA is currently active at US Federal, State, and local government levels, to gain acceptance and standardization of regulations based on ISA/IEC 62443. ISA is also participating in programs to promote use of ISA/IEC 62443 in multiple countries around the world.




