This document is intended to provide the reader with an overview of ISA 62443-3-2, “Security Risk Assessment for Design”, as well as a summary of some methodologies that can be used to assist execution of the industrial automation control system (IACS) cyber security risk assessment work process requirements detailed in the standard. This risk assessment work process is applicable to many sectors, e.g. industrial process sector, building automation, medical devices, transportation sectors, electrical production, water treatment, etc. Risk management of the IACS starts with a proposed design that is based on company standards and practices and/or recognized and generally acceptable good engineering practice (RAGAGEP). It then requires the understanding of how to identify vulnerabilities, threats, consequences of a successful attack, ranking risks, and then implementing mitigating measures to lower risks to tolerable levels. The standard itself is considered a (RAGAGEP).
The standard can be summarized in two figures, both workflow diagrams. Figure 1 illustrates the overall work process, while figure 2 illustrates the detailed level risk assessment sub process shown in figure 1.
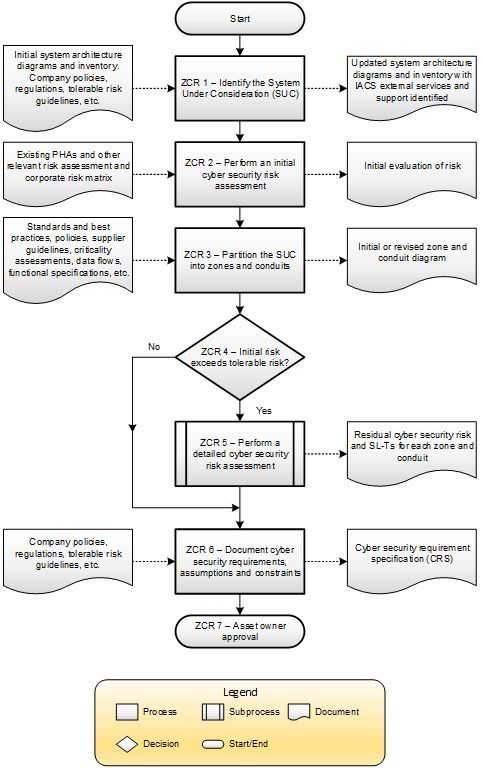
The major steps include:
- Identification of the System under Consideration (SuC)
- Perform an Initial Cyber Risk Assessment
- Partition the SuC into Zones and Conduits
- Perform a Detailed Level Cyber Risk Assessment
- Document Updated Cyber Security Requirements for Detailed Design
Each zone and conduit requirement (ZCR) number shown in figures 1 and 2 represents a specific requirement within the standard. The boxes in the left column of each figure represent inputs that are required for the different steps. The boxes in the right column represent outputs that are created in each step. The purpose of the cyber security risk assessment work process as a whole is to evaluate the consequences and associated likelihoods of risk scenarios due to security being compromised in order to prioritize which risks require mitigation as well as what cyber security measures are necessary to reduce the risk to tolerable levels established by the authority having jurisdiction, typically the operating company, referred to as the asset owner in the 62443 series of standards.
Risk is considered to be a measure of human injury, environmental damage, and economic loss, loss of intellectual property or loss of privacy in terms of both the incident likelihood and the magnitude of the loss or injury. A simplified version of this relationship expresses risk as the product of the likelihood and the consequences (i.e., risk = consequence x likelihood) of an incident. With respect to safety, health and environmental risk, consequences are measured in the same manner, irrespective of whether they are due to a cyber-attack or due to more traditional risk assessments that in the past have not considered cyber security. Likelihood, however, can be thought of as a combination of vulnerabilities and the likelihood that a threat agent or source has the requisite skills, resources, and motivation to exploit the potential vulnerabilities or that vulnerabilities are unknowingly exploited by non-malicious human error.
During the initial cyber security risk assessment, likelihood is often expressed as a conditional probability equal to one, while detailed cyber security risk assessments must consider likelihood as an estimated frequency or probability. Cyber risk assessments should address uncertainty (at least qualitatively if not quantitatively) since not considering uncertainties can produce misleading and potentially dangerous decisions. Should a detailed level cyber security risk assessment be required, its work process is shown in figure 2 below.
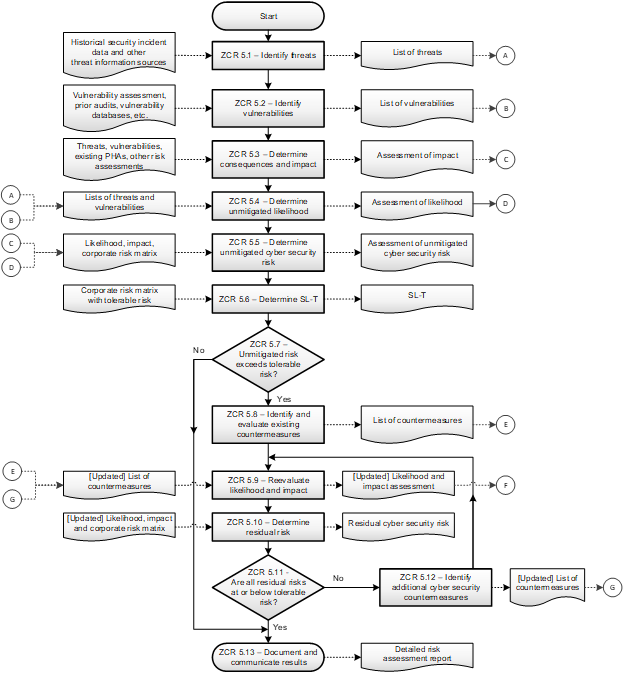
The ISA/IEC 62443-3-2 standard, entitled “Security Risk Assessment for System Design” was released in February 2020 and may be purchased either from the ISA, or the International Electrotechnical Commission (IEC). The benefits of using a risk-based standards approach include:
- Reducing the likelihood of a successful cyberattack
- The use of a common set of requirements among stakeholders
- Security throughout the lifecycle, and a
- Reduction in overall lifecycle cost.
Like most performance-based standards, it provides general requirements and is not prescriptive, meaning it defines what to do, but not how do it. The standard defines general requirements and links those requirements to examples of common best practices. For instance, it describes how to rank risk. Most corporations have a risk matrix that helps them establish their level of risk tolerance. Cyber risk assessments should be performed according to that basis and cyber risk, like any other corporate risk, should be ranked using that scale.
To support the “How” to execute the risk assessment requirements of the standard, this paper includes a summary of various methodologies for the performance of both vulnerability and risk assessments. More detail on these methodologies can be found in the source references. In addition, some guidance for application of the standard is provided to contrast green field projects versus brown field facilities.




