Securing operational technology (OT) networks requires a great deal of thought when designing and implementing security. Industrial networks contain a complex mix of specialized protocols and devices, including proprietary protocols developed for specific families of industrial automation devices.
This heterogeneous mix complicates security for OT environments. To structure this immense heterogenous environment, what is required to have exact reflection of inventory almost in real-time and network discovery comes into light.
What is Network Discovery in OT?
Network discovery is the process of identifying and detailing every OT and Internet of Things (IoT) device connected to your network physically, virtually, remotely, or in the cloud. The process of auditing, cataloguing, and tracking assets is essential for configuration management, capacity planning, and risk reduction programs. As a result of discovery, you can create an asset inventory to feed into systems like Security Information and Event Management (SIEM), Information Technology Asset Management (ITAM), and IP Address Management (IPAM) for a comprehensive view of your industrial control system (ICS) or industrial automation control system (IACS) network.
Why Is It Important?
Network discovery helps with full visibility into your environment through your asset inventory. Discovering new assets connected within the network is critical to maintaining the system’s integrity. This can help in detection of assets and provide a platform for where the risk can be reduced by tracking the threats or critical events across the network. On top of that, you need useful information that tells you what the device is, not just its media access control (MAC) address or operating system.
Challenges with Network Discovery
As the number and types of devices coming online are rapidly growing, organizations are struggling to effectively discover and inventory their network. Some organizations rely on a combination of solutions—like their vulnerability scanners and network performance monitoring tools—and are manually tracking their assets through spreadsheets. This process doesn’t scale, and the results are incomplete.
There are 4 major challenges across ICS or IACS environments:
- Most of the OT environments were designed and implemented around 30 years ago, and much of the technology in use is often legacy or running on unsupported operating systems.
- Air-gapped or isolated systems: With limited network connectivity and spanning across multiple networks, discovering these networks is the most critical job.
- Lack of full coverage: There are other information technology (IT) asset management tools out there, but again, most rely on credentials or endpoint agents to effectively inventory and map networks. Deployment is complex, and the results don’t include unmanaged devices.
- System impact: Confidentiality, integrity, and availability (also known as the CIA triad) plays a key role on network scanning. System failure can lead to human injury, environmental disaster, damaged equipment, and physical process downtime, all of which could impact large portions of the population. For these reasons, systems must operate for long periods of time with minimal maintenance windows. Security controls in these environments are designed to focus on ensuring uptime and availability, with marginal thought to confidentiality of data or data loss.
Asset Discovery Within the Network
There are several approaches for finding devices on the network. Because network inventory is an important part of many other OT and security functions, many vendors have network discovery built into their solutions. These tools include port scanners, vulnerability scanners, network performance monitors, and endpoint detection and response solutions. However, because asset inventory is not their main goal, their discovery capabilities are limited. These solutions don’t provide enough granularity and accuracy to provide a complete picture of all the assets on the network.
With asset inventory, organizations need to maintain a list or database of all IACS hardware (both physical and virtual) and software. Compile the asset list using documentation and site survey. This is not a trivial task, especially if it has not been done before and the company has been around for several years. There are automated tools that can be used to gather the data. However, automated tools should be carefully tested to ensure they do not impact system availability or integrity. They also should not introduce security vulnerabilities.
Asset inventory has three tools (see Figure 1):
- Network Management Tools (NMT)
- Software Asset Management (SAM) Tools
- Configuration Management Tools (CMT)
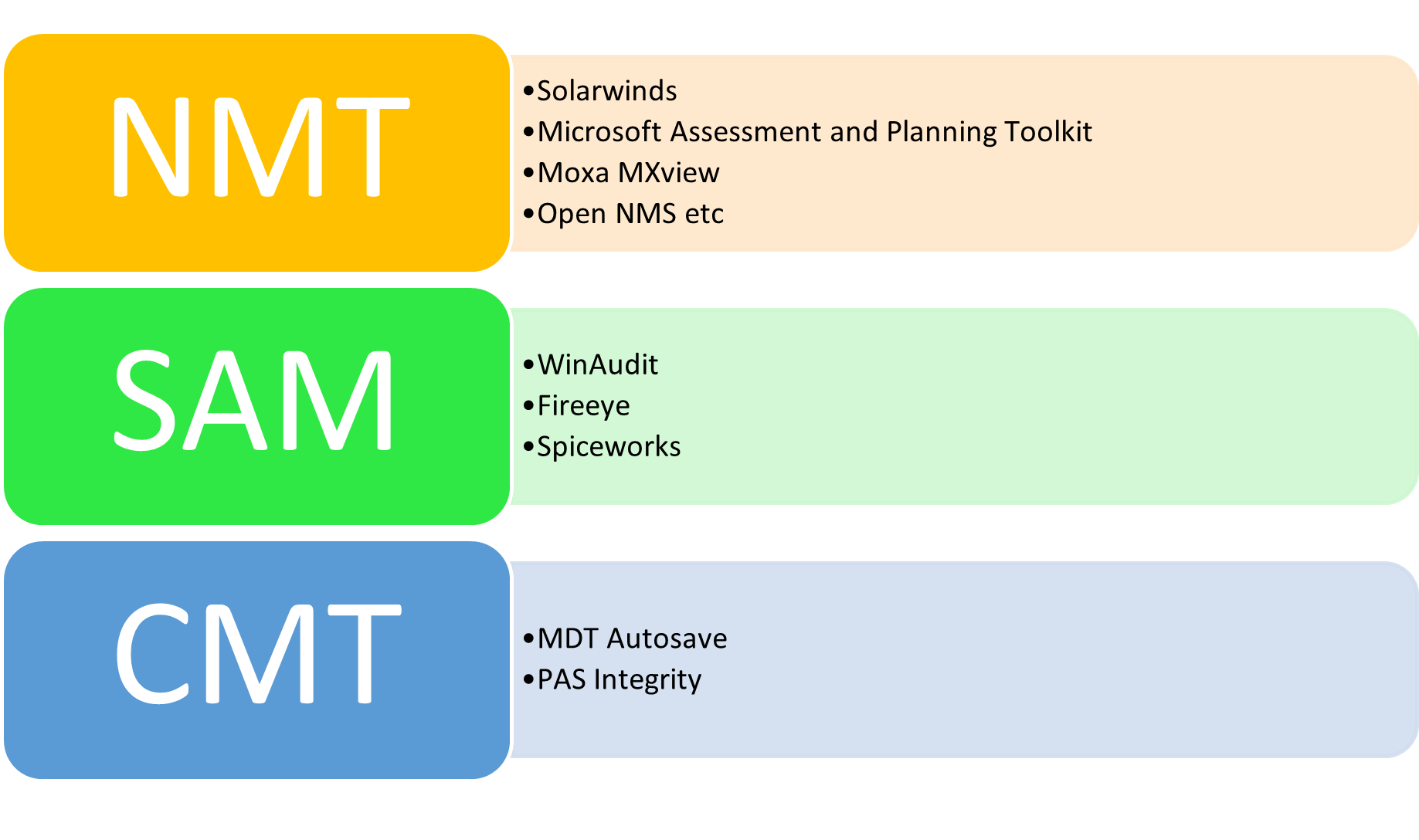
Figure 1: Examples of Asset Inventory Tools
Each tool has a critical section (i.e., network discovery). There are three categories on how a network discovery can be performed:
A. Active Network Monitoring - Network Scans (Active or Invasive Vulnerability Assessment)
This involves contacting each internet protocol (IP) on the network, on every port, to find active devices with open ports. This can find all devices on the network, not just the managed ones.
Benefits:
- Easy to deploy
- Detects managed and unmanaged devices
- Doesn’t require agents
- Doesn’t spray credentials across the network
- Works well with majority and cross platforms
- Free or commercial solutions available
Challenges:
- Can destabilize network sensitive devices
- Provides limited visibility into IoT, legacy, and guest devices
- Doesn’t require agents
- Can impact on system performance
- Security risk for safety systems or other critical OT process
- Free or commercial solutions available
B. Agent-Based Discovery
Agent-based solutions requires the installation of agents on each device. Due to the agent’s wider visibility and interconnectivity, the solution can inspect processes, file systems, memory, and the windows registry to infer software installed on devices, as well as detect malware. These solutions typically are Endpoint Detection and Response (EDR) solutions and Configuration Management Databases (CMDB) or SIEM solutions.
Benefits:
- Identify wider systems across the network
- Advance detection capabilities
- Multiple third-party plugins available for wider monitoring functionalities
Challenges:
- Requires deploying agents to each managed device
- Updating each agent can be time-sensitive
- Assets not categorized (like Industrial Internet of Things (IIOT) or legacy, etc.)
- Too many agents can slow down the system
- Agents may not be available for all platforms in use
C. Passive Network Monitoring
This discovers network devices using means including reviewing drawings, system walkthroughs, traffic analysis, and Address Resolution Protocol (ARP) tables. To monitor the network, these solutions need to tap Switched Port Analyzer (SPAN) ports, which can be very difficult to set up in complex networks. With passive network monitoring, solutions can only hear devices that talk on the network. Devices that don’t generate network traffic can’t be discovered with this tool.
Benefits:
- Works well with OT networks
- Most trusted approach on a busy network
- Advance detection capabilities
- Multiple third-party plugins available for wider monitoring functionalities
Challenges:
- Difficult to deploy on legacy network infrastructure
- Doesn’t scan inactive ports or devices
Conclusion
Network discovery is a critical building block of any cybersecurity program, and the method you choose should be the foundation of your OT cybersecurity program. It is certainly work exploring all the options and perform proof of concept (POC) to identify which solution works better for your organization’s network. Always remember, “Security is not a solution, but it’s a habit; you have to keep updating yourself with time.” The solution you go should be adaptable to future security requirements.
References
[1] Patrick Kelley, “Asset Discovery Challenges in OT and ICS Environments,” [Online]. Available: https://www.axonius.com/blog/asset-discovery-challenges-ot-ics-environments. [Accessed 29 March 2022].
[2] N-ABLE, “What is Network Discovery,” [Online]. Available: n-able.com/what-is-network-discovery [Accessed 29 March 2022].
[3] Roberto Ceron, “Overcoming challenges with discovery and inventory of remote IT assets,” [Online]. Available: https://blog.shi.com/business-of-it/overcoming-the-challenges-with-it-discovery-and-inventory-of-remote-it-assets/ [Accessed 29 March 2022].




