Misconceptions about ICS/OT cybersecurity are stubborn. This "mythbusting" blog series dispels five common myths related to ICS cybersecurity. Catch up on the series if you're interested:
- Common ICS Cybersecurity Myth #1: The Air Gap
- Common ICS Cybersecurity Myth #2: Proprietary Systems and Protocols
- Common ICS Cybersecurity Myth #3: The Unbreachable Firewall
Now, let's dive in.
ICS Cybersecurity Myth #4
Serial communication (non-routable) between a control center and remote sites (such as onshore oil rigs, electricity substations, or mines) provides immunity from cyberattacks
Serial communications such as RS-232 or RS-485 are logically isolated communication methods that provide controlled communications. There is a common assumption that any serial communication (non-routable and not over Ethernet/TCP/IP) is intrinsically secure and protected from cyberattacks.
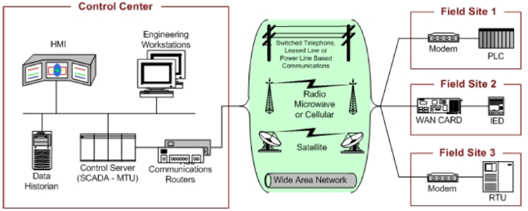 Source: NIST SP 800-82
Source: NIST SP 800-82
Busting ICS Cybersecurity Myth #4
Serially connected remote industrial sites or substations typically have two networks for operations: one serial network to the control center and another local IP/Ethernet network for plant/substation OT communications. Usually there is also a third IP network for corporate purposes, such as email, web browsing, and so on.
To attack from the outside, it is true that attackers need access to externally routable devices and/or protocols. Recent incidents, however, have demonstrated that it is possible to compromise a serially connected remote site through other means. Attackers can find and exploit vulnerabilities via the corporate network (if the firewall is misconfigured), USB, transient systems, social engineering, third-party suppliers, or a physical security breach. Certainly, it is not that straightforward and requires additional efforts—attackers need to find bridging points where one network device deals with both IP and serial (i.e. serial-to-IP converters) or a firewall that segregates OT and corporate networks.
Many organizations use dial-up connections for emergency access to remote sites. If compromised by attackers, these could also allow unauthorized access. Most dial-up connections use older, legacy devices that are harder to protect.
Serial communications alone do not provide immunity from cyberattacks. In December 2015, unidentified hackers caused a power outage in Ukraine, in part by attacking serial-to-Ethernet converters—which, like any other devices, are vulnerable to remote attacks and compromise.
Recently, attackers also tried to convince and bribe a Tesla employee to plant malware inside Tesla’s network. The plan was to steal information, trigger a DDoS attack, and demand ransom. The attackers offered the employee up to 1 million USD to be paid in cash or Bitcoin. Fortunately, the employee did not get trapped, and instead reported the attempt to Tesla. Tesla contacted the FBI, and the alleged attacker was caught.
Just like what could have happened to Tesla, similar scenarios could play out at any remote industrial site and substation—despite having serial-based remote connections. Attackers can either breach physical security or possibly try to social engineer employees, planting a “wireless rogue device” to cause damage or outages at a later time. Due to a lack of remote monitoring, the control center team may not even know about the presence of such rogue devices.
Stay tuned for the next part in this series, in which we break down Myth #5: the belief that there is not much for hackers to gain by attacking industrial networks.
Interested in reading more articles like this? Subscribe to the ISAGCA blog and receive weekly emails with links to the latest thought leadership, tips, research, and other insights from automation cybersecurity leaders.




