Cybersecurity incidents continue to increase in frequency and have greater impacts on the critical infrastructure of nations around the world. Incidents associated with operation technologies (such as automation and control systems) are impacting industries, governments, and other parties. The implementation of the ISA/IEC 62443 series of international cybersecurity standards can help prevent incidents and minimize the disruption and impact of incidents that occur. These are some incidents that have significantly impacted critical infrastructure:
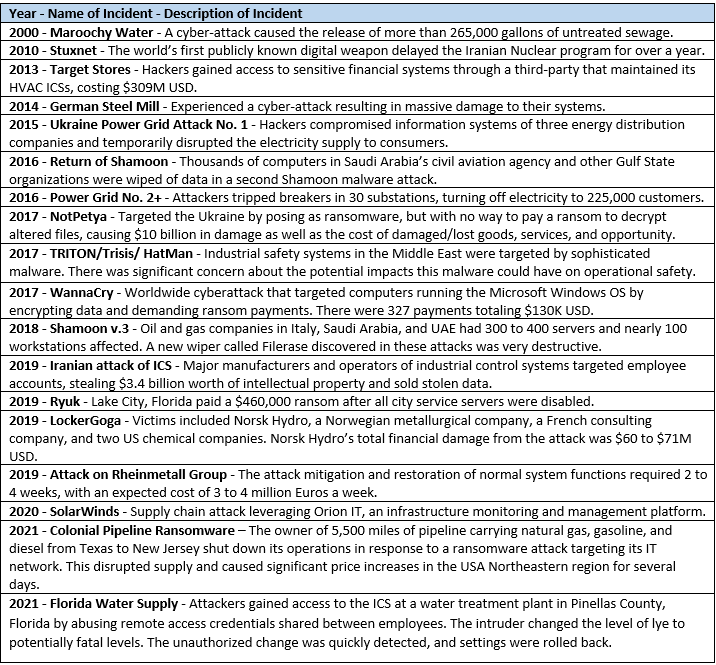
These are some of the incidents that were prevented and/or minimized by following good cybersecurity practices, like those defined in ISA/IEC 62443:





