The ISA Global Cybersecurity Alliance (ISAGCA) recently released a guide to security lifecycles in the ISA/IEC 62443 Series. To give you a brief taste of the content you can find in the guide, we republished its executive summary below. Understand more about the different security lifecycles outlined in the world's only consensus-based automation cybersecurity standards and download the full guide at www.isa.org/securitylifecycles.
Executive Summary
This document provides an overview of the security lifecycles that are described in the ISA/IEC 62443 Series of standards and technical reports, which specifies the requirements for the Security of Industrial Automation and Control System (IACS). There are two security lifecycles that are included in the ISA/IEC 62443 Series: the Product Security Lifecycle and the Automation Solution Security Lifecycle.
The Product Security Lifecycle specifies the security requirements for the technical and organizational security measures used to design, develop, and support IACS System and Component products. It includes secure by design aspects such as threat modeling and defense-in-depth strategies, secure implementation such as secure coding standards, security verification & validation testing, and security update management. Technical security measures based on Security Levels allow the Product Supplier to deliver IACS Systems and IACS Components that are capable of meeting specified security requirements, provided the Asset Owner maintains associated organizational security measures.
The Automation Solution Security Lifecycle is shown in Figure 1 and specifies the technical and organizational security measures used throughout the lifecycle of the IACS Automation Solution, which is the realization of IACS Systems and IACS Components at a particular facility.
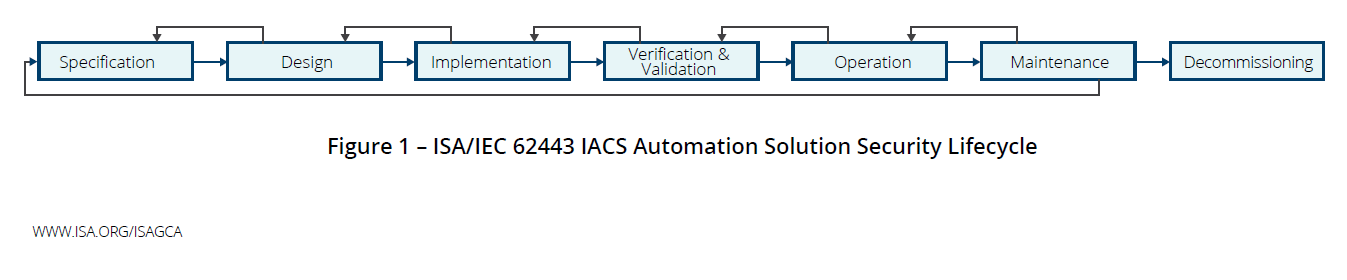
Diagram republished from ISAGCA's "Security Lifecycles in the ISA/IEC 62443 Series"
Asset Owner, Product Supplier, and Service Provider are roles that are defined later in this document. Roles are not the same as organizations. An organization can have multiple roles, and the responsibilities of a role can be split between multiple organizations. While this document presents typical roles and responsibilities throughout the security lifecycles, it is important to note that the Asset Owner must determine and document the actual roles and responsibilities used for their organization and IACS Product Suppliers and Service Providers.
There are a few key messages that the reader should understand from this document:
- The Asset Owner is accountable for the cybersecurity risk of the IACS and the Equipment Under Control
- IACS cybersecurity is a shared responsibility among Asset Owner, Product Supplier, and Service Providers
- IACS cybersecurity is required throughout the Automation Solution Security Lifecycle
- IACS cybersecurity is required throughout the Product Security Lifecycle
If you'd like to read more, please request your free copy of "Security Lifecycles in the ISA/IEC 62443 Series: Security of Industrial and Automation Control Systems" at www.isa.org/securitylifecycles.




