Many professionals have wrong concepts regarding zones and conduits, the way in which they must be defined, and their implications from the point of view of industrial cybersecurity. A good understanding of zones and conduits is of fundamental importance to avoid making mistakes in risk evaluation, design, implementation, and maintenance.
The concept of zones and conduits was introduced by the ISA99 committee of the ISA/IEC 62443 series of standards, a long time before the first versions of the standard were published in 2007. Today we see that many other organizations use these same terms in different ways, increasing confusion for users and professional communities.
Zone: consists of the grouping of cyber assets that share the same cybersecurity requirements
Conduit: consists of the grouping of cyber assets dedicated exclusively to communications, and which share the same cybersecurity requirements
When modeling zones and conduits, there are a series of important rules that professionals must take into account. Below, we share some practical rules that will be useful:
- A zone can have sub-zones.
- A conduit cannot have sub-conduits.
- A zone can have more than one conduit. Cyber assets (HOSTs) within a zone use one or more conduits to communicate.
- A conduit cannot traverse more than one zone.
- A conduit can be used for two or more zones to communicate with each other.
Let's look at these rules in the following chart. It demonstrates examples of correct and incorrect setups, as well as examples of conduits.
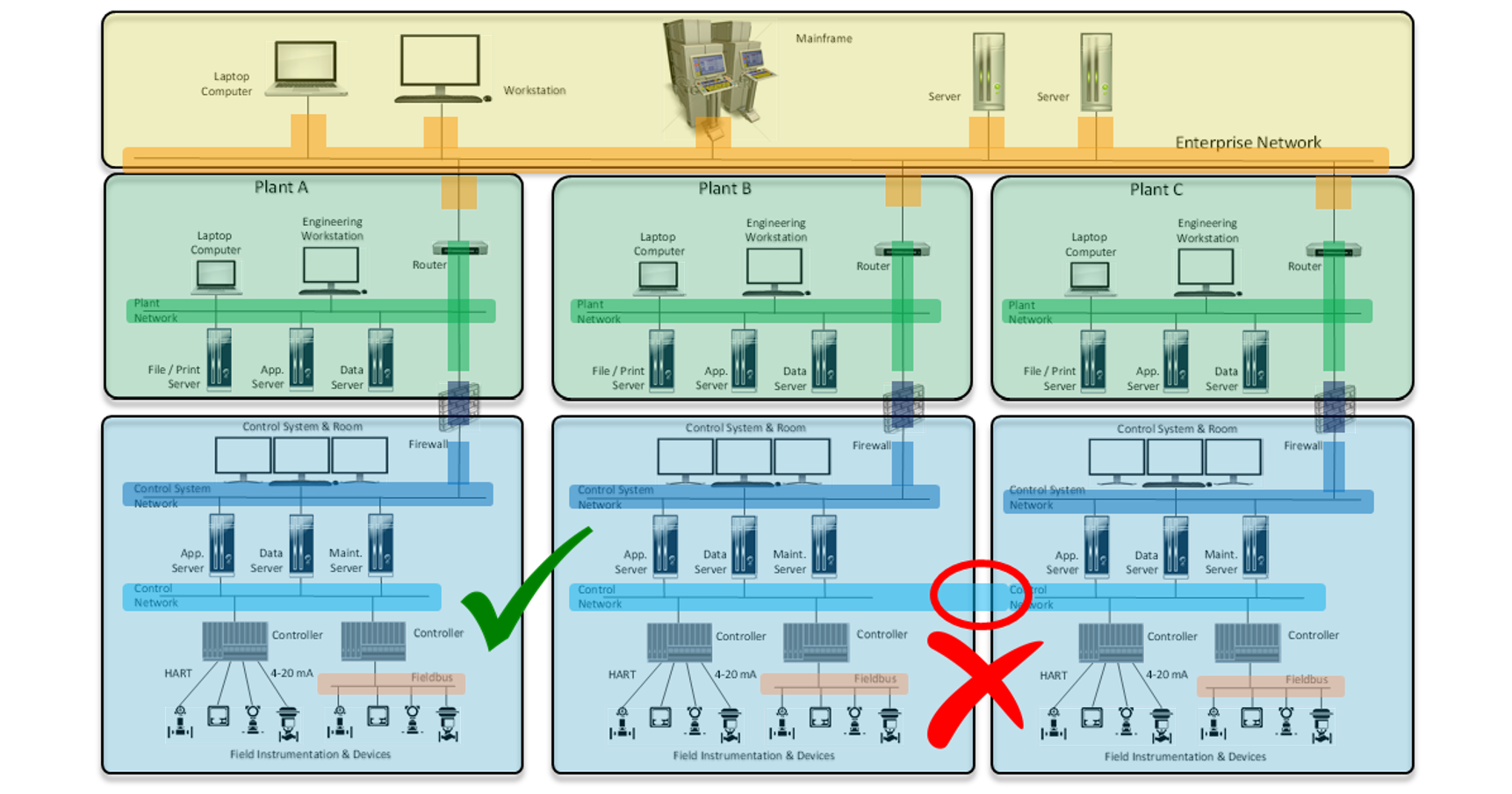
Industrial cyber assets have a very special feature—they can connect to more than one conduit, often to several conduits at the same time. A PLC can easily connect to 10 or more conduits. It is important to consider that many industrial networks are of the redundant type.
Some Common Types of Conduits
Industrial systems have hundreds of protocols in different media, if not thousands of protocols of all kinds, nature, and function. Many of them are deterministic, among other technical qualities that are not worth mentioning here.
- Plant network based on Ethernet with various industrial protocols, including OPC
- Control network of the distributed control system (Example: Yokogawa Centum VNet/IP)
- Industrial field network (Example: Profibus DP, DNP3, and many others)
- Industrial field network: Foundation Fieldbus, HART7, and others
- Wireless network: ISA100, Wireless HART, and others
- A simple RS-232/422/485 serial cable to enable communication between two computers
Initial Segmentation
Before Carrying Out the Detailed Risk Assessment (Cyber-PHA)
ISA/IEC 62443 suggests a series of minimum or elementary criteria to carry out an initial zone and conduit segmentation before conducting a detailed cyber risk study, also called Cyber-PHA (Cyber Process Hazardous Analysis), Cyber-HAZOP, or Cyber-LOPA. Many people believe that the recommendation is all that must be done, but they are mistaken. The recommendation is correct, but it is not enough.
Optimal Segmentation
After Completing the Detailed Risk Assessment (Cyber-PHA)
Once the detailed risk assessment has been carried out, there will be an optimal segmentation of zones and conduits, together with an often-extensive list of recommendations and countermeasures. Simple segmentation is necessary, but in itself, it is not sufficient. A series of recommendations must accompany the optimal segmentation. Each zone or conduit (node) will have an SL-T-required security level (Security Level Target), and an SL-A current security level (Security Level Achieved)—all without going into much technical detail.
This post originally appeared on the WisePlant blog. It is republished here with the permission of its author.
Interested in reading more articles like this? Subscribe to the ISAGCA blog and receive weekly emails with links to the latest thought leadership, tips, research, and other insights from automation cybersecurity leaders.




