At the ISA Global Cybersecurity Alliance (ISAGCA), we seek to increase global awareness and understanding of the ISA/IEC 62443 Series of Standards, the world's only consensus-based automation cybersecurity standards. Our latest efforts focus on defining the principal roles and responsibilities involved in an industrial and automation control system (IACS).
Our latest resource is a short explainer document called the "IACS Principal Roles and Responsibilities." We created it to help build a common basis of understanding for anyone reading or seeking to use the 62443 standards. The document establishes the roles of asset owner, maintenance service provider, integration service provider, and product supplier. It also visualizes their responsibilities as defined in 62443.
As another avenue of education, ISAGCA is sponsoring a webinar on 27 January 2021 called "Automation Control Systems Cybersecurity: Lifecycles and Responsibilities." Topics to be covered include:
- IACS security, ICS security
- Security lifecycles
- Roles and responsibilities
- ISA/IEC 62443 Series of Standards
- Secure facilities, secure processes, secure devices
Download the IACS Roles and Responsibilities Document
You can access the complete Roles and Responsibilities document by clicking on the image below. It's a free download that is open to all.
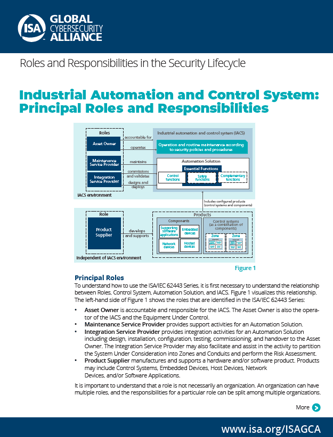 The document is also accessible here in full: IACS Principal Roles and Responsibilities
The document is also accessible here in full: IACS Principal Roles and Responsibilities
Other ISAGCA resources created so far include the "Quick Start Guide to the ISA/IEC 62443 Series of Standards," a guide called "Security Lifecycles in the ISA/IEC 62443 Series of Standards," and the "IACS Taxonomy Definitions of Terms." All ISAGCA guides and explainers are free to download and share with your team.
Attend the IACS Lifecycles and Responsibilities Webinar
The ISAGCA-sponsored webinar will take place on 27 January 2021 at 12 p.m. EST/9 a.m. PST. It will explore how to apply ISA/IEC 62443 standards documents to each phase within the security lifecycle, and it will outline core responsibilities that various roles must take on to protect systems and facilities.
Attendees will also receive a high-level view of two key lifecycle concepts presented within the series of standards: the Product Security Lifecycle and the Automation Solution Security Lifecycle.
The speaker will be Johan Nye, author of both of ISAGCA's guides to ISA/IEC 62443. Nye is an independent consultant specializing in industrial control systems (ICS) and cybersecurity. During his career spanning more than 38 years, Nye has designed ICS system architectures, created company standards and policies, implemented major ICS projects, supported ICS site engineers, and contributed to the design of several ICS products.
To register for the webinar, please visit this signup page.
Interested in reading more articles like this? Subscribe to the ISAGCA blog and receive weekly emails with links to the latest thought leadership, tips, research, and other insights from automation cybersecurity leaders.




