The methodology for evaluating industrial cyber risks has been the subject of much debate ever since the topic began to be discussed. However, it is crucial for industrialists to adopt the correct methodology. There are those who have a great deal of experience in information security and seek to apply the same practices and formulas in industry, and there are those who know that this approach is insufficient and inappropriate.
Risk management methodology is used to make decisions, define the actions that need to be implemented to mitigate risk, and justify investments.
If two risk management methodologies suggest different decisions, then at least one of them is wrong or insufficient.
The methodology proposed by the ISA/IEC 62443 series of standards complies with the RAGAGEP (Recognized and Globally Accepted Good Engineering Practices) requirements. Because industrial cybersecurity is immersed in the domain of physical security, with serious and very dangerous consequences and impacts on the physical world, this is an issue of substantial importance.
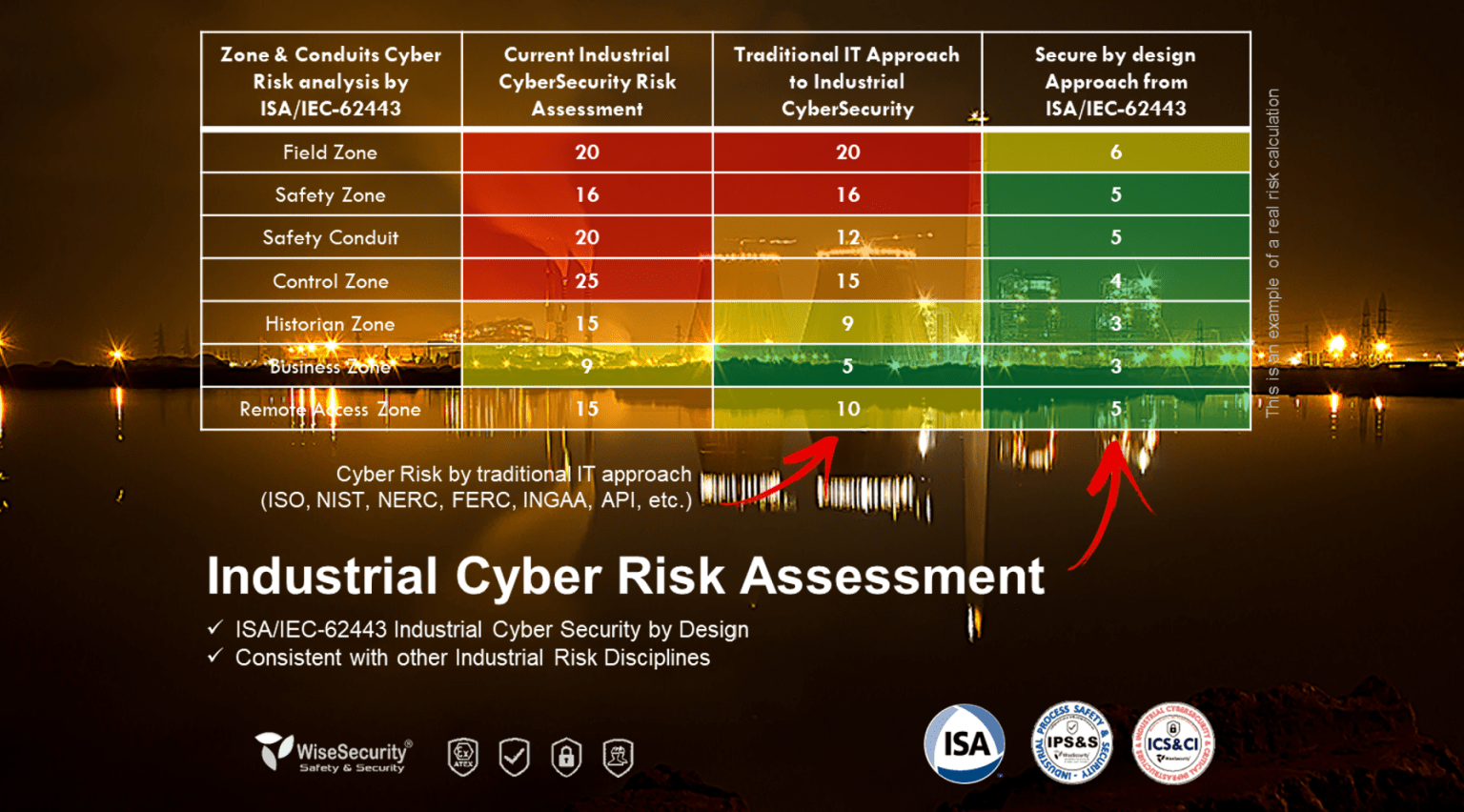 Diagram courtesy of WisePlant
Diagram courtesy of WisePlant
In turn, industrial cybersecurity must share the same resources as other multiple disciplines of industrial risk, such as functional safety, intrinsic safety, environmental safety, human safety, HACCP, FDA (food and pharmaceuticals), and many others depending on the industry.
It is essential that risk mitigation actions are consistent across all these disciplines and do not compete with each other. On the contrary, they should be enhanced, not canceled out. You cannot improve one risk discipline to the detriment of another. Industrial safety cannot be approached asymptotically or systematically as a “trial and error” process. Human lives are at stake, among many other dangers.
NIST, NERC, Etc. (Traditional IT)
Security of the Information
This approach is based on statistical data, taking the number of market incidents grouped by industrial segment and an assessment of the severity of vulnerabilities.
It does not take into account the needs of the other industrial risk disciplines. It addresses the organization as a whole, without differentiating the most critical processes from those less critical processes. It considers all processes to be of the same criticality.
- Less critical processes are loaded with greater security measures than necessary, dedicating more resources than necessary. The contribution to risk reduction is low. The excess of security measures in the less critical processes does not reduce risk.
- The most critical processes are actually less protected, not contributing to the real and minimum necessary effective reduction of risk.
This methodology for decision making seems to make sense in statistics, but in practice, resources are not distributed appropriately. You overspend where you don't need to, and you underspend where you really need it.
It does not take into account all risk recipients for decision making. It does not take responsibility for the safety of people, safety of the environment, and so on. It is limited to information and data security. You don't have a way of measuring how much your decisions contribute to risk reduction for all risk takers.
ISA/IEC 62443 (RAGAGEP)
Consequence-Based Security
This approach is based on the consequences of each process and the potential impacts for each of the risk recipients. It is a multidisciplinary process consistent with the other disciplines of industrial risk.
Approach each process individually, partitioning into zones and ducts, making decisions based on the criticality of each process individually. Prioritize the most critical processes from the least critical.
- In the most critical processes, greater security measures are taken, proportional to the potential impacts.
- Countermeasures can be technological, administrative, and physical.
- This approach incorporates security by design, where the mitigation of a cyber risk can result in a physical modification of the plant.
This methodology for making security decisions values and incorporates the measurement of the potential impacts on each of all the risk receptors and for each of the processes. Security efforts are optimally distributed with a necessary and sufficient contribution to risk mitigation in the physical security domain.
It considers and evaluates all possible types of threats that could compromise the security of the industrial technological infrastructure—for example, external/internal, intentional/non-Intentional, technological, human-based, and natural.
Some Additional Observations
- The traditional approach to IT does not prioritize availability in the same way that industrial systems require it. The most critical information technologies can reach a maximum of four to five nines, while in the most critical and dangerous industrial systems, availability has a minimum of seven nines. The IT world is not used to working with systems of a deterministic nature and very high availability, among many other differences.
- On the other hand, information systems accept risk coverage by the insurance company much more quickly. In the industrial field, this is not a sufficient approach. We have to deal with people's lives and permanent damage to the environment, among many other very serious risks. Explained in a clearer and more concrete way: for the operator who must go to work every day at the plant, it is of no use that the organization has insurance. Cyber risk tolerance is much lower and cannot be resolved by successive approximations.
This post originally appeared on the WisePlant blog. It is republished here with the permission of its author.
Interested in reading more articles like this? Subscribe to the ISAGCA blog and receive weekly emails with links to the latest thought leadership, tips, research, and other insights from automation cybersecurity leaders.




