This is Part 4 of The OT Security Dozen – a 12-part series on building an OT/ICS cybersecurity program for an industrial operations environment.
Note: You may have noticed that operational technology (OT)/industrial control system (ICS) cybersecurity awareness is a common theme across “The OT Security Dozen,” and hence no exclusive part on awareness itself. The aim for this series is to raise awareness on each type of controls covered, and therefore is considered an essential/integral necessity across this 12-part series.
This part is to help industrial end user/operator organizations understand the typical challenges and drivers behind selecting, implementing, and maintaining an OT intrusion detection (OT IDS) or anomaly detection (AD) solution for OT networks and how such solutions help address challenges around contextual visibility and situational awareness through the identification of assets, traffic flows, vulnerabilities, risks, and aids in continuous monitoring and incident response activities.
Assuming you've performed the OT Security Dozen Part 1: A Year of OT/ICS Cybersecurity Assessments with the discovery of assets and network diagram (and, ideally, having OT Security Dozen Part 3: Network Security Architecture & Segmentation in place, though not mandatory, which could potentially help in lowering the costs of solution implementation). Now we have all the essential pre-requisites for the site and technical information that is required to evaluate, select, implement, and run an OT IDS/AD solution to enhance an OT/ICS cybersecurity program.
OT Industry Challenge – Lack of Contextual Visibility
Historically, because of information technology (IT)-OT convergence, OT/ICS or production control networks lack contextual visibility in terms of what’s connected to the network and how traffic flows between the assets on the networks. Due to the increase in business demands for more efficiency, productivity, and connectivity requirements for Industry 4.0/industrial internet of things (IIoT)-related digital transformation initiatives, visibility challenges have compounded further. Until a few years ago, there were a handful of solutions with very limited or no capabilities of interpreting a wide range of industrial protocols and detecting anomalies, which required a lot of customization and advanced skillsets.
Other challenges associated with OT asset and traffic visibility are, but not limited to:
- No or outdated overall/central OT asset inventory and network diagrams maintained by the production facility.
- Lack of traffic visibility (or documented data/communications flow) across the OT network.
- Project-based OT asset inventory and network diagrams (sometimes only for part of the production facility, e.g., new production lines) are usually outdated and changes/updates are lost for various reasons (vendor/system integrator-provided diagram at time of commissioning, implementations done several years ago, people/vendors moved on, missing original copy, etc.).
- Engineering resources are tasked to manage individual production lines, causing a lack of knowledge and/or ownership to keep track of changes and updating documents.
Knowing what needs to be protected (assets discovery) and what the risks are (vulnerabilities and threats) are crucial for any IT or OT cybersecurity program, and, according to almost all international standards and best practices, are part of foundational controls that should be put in place.
Market Response – OT IDS/AD Solutions
Industries have responded initially with solution offerings addressing specific needs with point products (e.g., by original equipment manufacturer [OEM] vendors) addressing OT asset discovery/inventory challenges and/or specialized products addressing anomaly detection challenges. Later, industries saw the rise and emergence of specialized security solutions, quickly recognizing the market demands to bundle both the visibility and detection capabilities. In the last 6 years or so the number of such security vendor solutions has dramatically increased by the emergence of niche players entering this space and raising millions in funding and/or traditional global networking or software names either building or acquiring such specialized solutions and integrating them into their product portfolio.
The last 2 years of the pandemic saw an accelerated growth in terms of the maturity of such solutions, expanded OT protocol coverage, greater accuracy in asset, vulnerability, and anomaly/threat detection, and other added capabilities (e.g., internet of things [IoT], IIoT, or internet of medical things [IoMT] device visibility). These solutions are now available in different forms such as on-premises hardware, software-based solutions, or containerized in networking gear and managed via software as a service (SaaS) based portals.
The below diagram depicts a list of a few cybersecurity challenges faced by an industrial organization and how OT IDS/AD solutions address them across PREDICT, PREVENT, DETECT, and RESPONSE cycles (at a high-level):
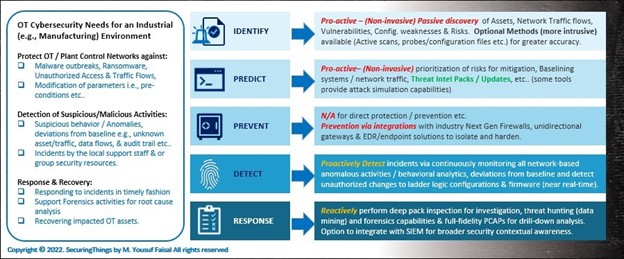 Figure 1: OT cybersecurity challenges and how OT IDS/AD solutions help address them
Figure 1: OT cybersecurity challenges and how OT IDS/AD solutions help address them
OT/ICS Cybersecurity Programs & Mapping to Industry Standards
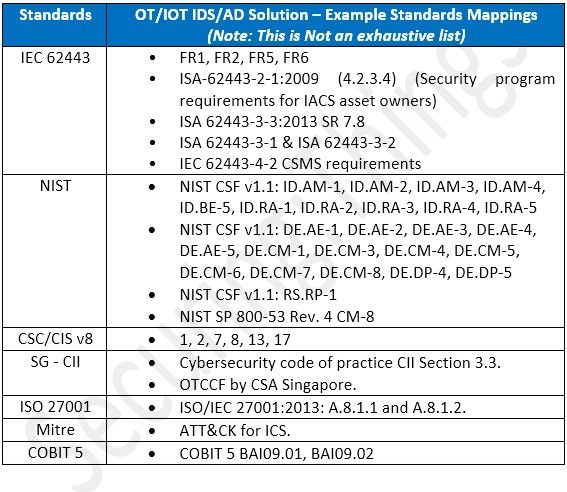 Figure 2: OT/IoT IDS/AD solutions – Example of standards mapping
Figure 2: OT/IoT IDS/AD solutions – Example of standards mapping
Pre-Requisites and Things to Consider
There are several key prerequisites for implementing an OT IDS/AD solution for OT environments (e.g., manufacturing). Some important considerations include:
- Critical senior leadership support (allocation of funds and resources).
- Full discovery should be done for the sites in scope and site readiness validated.
- Target monitoring scope should be clearly defined, such as with coverage for north-south and east-west OT traffic (e.g., OT demilitarized zone [DMZ], across production lines, warehouse, building management, lab, etc.).
- Collaboration and coordination in terms of resources identified with clear responsible, accountable, consulted, and informed (RACI) goals and a support structure plan between IT/OT teams.
- Support from OEM vendors, system integrators, and/or suppliers that run/operate/support production and associated network facilities.
- The management of collected data, its security, and privacy.
OT IDS/AD Solution Comparison & Selection
There are several different OT IDS/AD solutions available in the market with support to provide coverage across IT, OT, IoT, and IIoT devices/systems. Below is a high-level list of OT IDS/AD solution evaluation and selection criteria (in no particular order).
Note: While comparisons are good, conducting proof of concept (POC) and viewing the outcome is the best way to select a solution; narrow down to at least the top two solutions for POC.
- Most critical: Alignment with end user OT/IoT specific environment variables (network architecture, OT protocols used and its support, and below elements).
- Accuracy and performance: Identifying assets, ability to create baselines, and the mapping of networks (traffic flows between zones/conduits and detecting anomalies).
- Data sources and coverage: IT/OT/IoT/IIoT and protocol coverage.
- Methods and techniques: Passive, active probes, config parsing, etc.
- Scalability and integration: Ease of scaling up/down and integration with existing IT/OT technology stack.
- Alerting, reporting, and dashboards: Baseline deviations, security/operational alerts, risk reporting, customizable local/global summary/dashboards, etc.
- Support and maintenance: Technical support, frequency of updates, documentation, training, etc.
- Costs and return on investment (ROI): Both direct and indirect costs of hardware, licenses, subscriptions, annual maintenances, and services (i.e., implementation, fine tuning, maintaining for both external/internal resources).
- Mapping to industry standards: ISA/IEC 62443, NIST CSF, CSC20 (now rebranded as CSC18) and/or the MITRE ATT&CK framework.
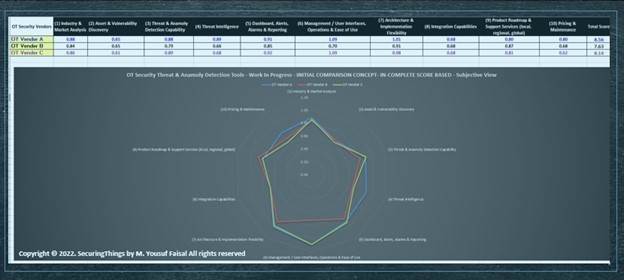 Figure 3: Example OT IDS solution comparison scores with spider chart
Figure 3: Example OT IDS solution comparison scores with spider chart
OT IDS/AD – Methods & Techniques
There are a few different methods that can be used by OT IDS/AD solutions, including passive, active, and configuration file methods. Each of these methods has its own unique characteristics and advantages, and they can be used alone or in combination depending on the specific goals and objectives defined.
- PASSIVE discovery is nonintrusive, easy to configure, and in real-time.
- ACTIVE scans/probes will query assets and is especially good at finding the details about windows devices that passive will miss.
- Parse device configuration files will parse device configuration files to reconstruct an inventory.
- Application programming interface (API) integration to discover infrastructure and connected devices.
OT IDS/AD solutions may leverage a combination of statistical analysis, machine learning, and artificial intelligence (AI) techniques for enhanced detection and alerting capabilities.
OT IDS/AD Solution Implementation Types/Scenarios
The following diagram highlights a few examples of both on-premises and hybrid implementations in a 2-tier or 3-tier architecture models for a single site and/or multi-site global deployment.
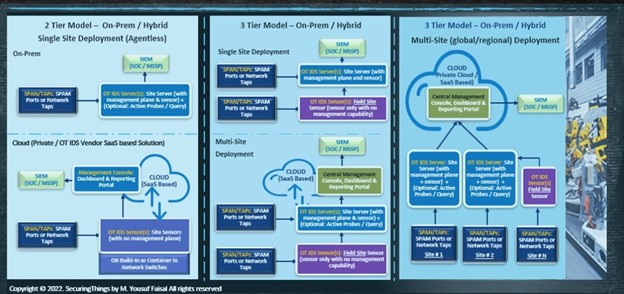 Figure 4: Example OT IDS/AD deployment architecture types
Figure 4: Example OT IDS/AD deployment architecture types
Define Success Criteria
Define success criteria early in the project lifecycle across the following:
- Project execution/deliverables across each project stage
- For solution running in learning/monitoring/training mode
- For solution running in alerting/audit mode
OT IDS/AD – POC & Implementation
The implementation of an OT IDS/AD solution typically involves several steps or stages. Some of the key steps involved in both running a POC and/or deploying/implementing an OT IDS/AD solution are depicted in the following diagram.
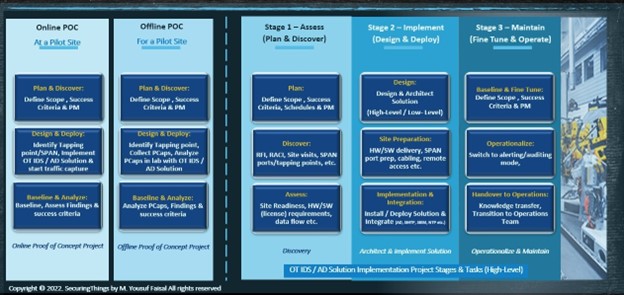 Figure 5: OT/IDS POC options and OT/IDS implementation project stages
Figure 5: OT/IDS POC options and OT/IDS implementation project stages
Note: The two types of POC approaches can be adapted: Offline POC and Online POC. The key difference between two is that one is implemented in a lab environment with the use of PCAPs, and the other is performed on site at a production facility.
OT Cybersecurity Program & Processes
OT IDS/AD solutions, once implemented, becomes one of the main key OT log sources, providing comprehensive details for network-based activities/events and generating alerts for which organizations need to have a plan in place for handling those alerts effectively, which should include:
- Prioritizing and triaging alerts
- Investigating and determining the cause of the alert
- Implementing a response plan
- Monitoring and evaluating the response
- Where required, update policies and procedures accordingly
After implementation, organizations can take several steps to run and improve OT cybersecurity programs, which may include:
- Developing guidelines to effectively manage and run the solution
- Regularly review and update policies and procedures
- Conducting regular assessments and audits
- Train and educate personnel responsible for interacting with the solution
- Implementing controls and measures to protect the solution
Documenting the Deployment – Solution Design & Implementation (Configs & SOPs)
Document entire project lifecycle: It’s critical to understand the importance of documenting the discovery, design/architecture, implementation details, and standard operating procedures (SOPs) for managing the solution. The following diagrams highlights the essential elements (as an example only, not an exhaustive list) to be documented, maintained, and kept up-to-date (create and maintain a single or set of documents based on organizational practices).
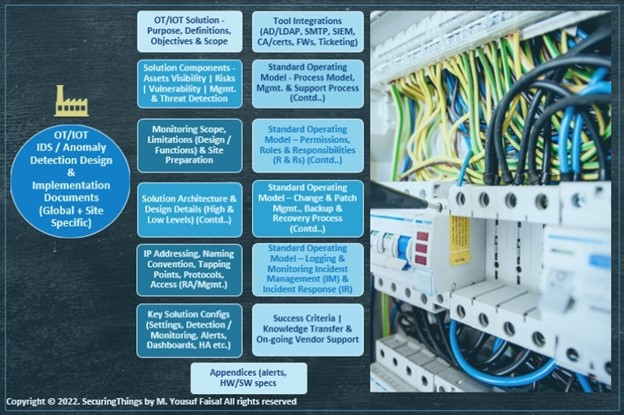 Figure 6: Example of OT IDS/AD solution design and implementation document
Figure 6: Example of OT IDS/AD solution design and implementation document
Knowledge Transfer Overview
After OT/IDS solutions have been implemented, ensure that there’s a hand-over between the implementation and operations team that will be running and managing (plus monitoring) the solution. A good way to do this is to arrange a knowledge transfer session between the teams covering the following topics:
- A brief on solution components and functions
- Solution implementation design/architecture
- A brief introduction on basic and advanced functionality
- Processes and support for smooth operations
Note: This is not supposed to be a training alternative. For product training, look for OT IDS/AD vendor-specific training options.
Recommendations, Key Takeaways, and Next Steps
Avoid common failures with addressing needs across asset visibility, solution selection, and implementation and operationalization by:
- Ensuring that the pre-requisites aforementioned are addressed with full commitment from executive management
- Don't get hung up on solution comparison. Instead, go with the tools that meet your requirements and budgets (a “feature war” is for another day; if you are not going to use a certain functionality, why worry or invest in it?).
- Don't solely rely on solutions. Validate discovered assets by physical inspection/observations and update/tag corrections in asset inventory.
- Ensure that resources are allocated and build processes around the solution for continuous monitoring and improvement.
OT IDS/AD solution is also a key security control solution for any given OT cybersecurity program, directly or in-directly improving or facilitating the following security processes:
- Asset management (identification and inventory)
- Network segregation (identify data flows between zones and systems)
- Vulnerability management (identification and tracking)
- Configuration hygiene (identify configuration weaknesses and insecure protocols)
- Cybersecurity monitoring (detection and alerting)
- Incident response (to security incidents and breaches)
- Compliance (with applicable regulations, standards, and internal policy).
For your industrial operations, select, design, and implement an OT IDS/AD solution for contextual visibility of OT network environments. If you are unsure where to start, engaging an expert is your best bet to help you select and implement the right OT IDS/AD solution.
A version of this article originally appeared on LinkedIn. The author will be first featuring the series on this platform and encourages everyone to follow along in the SecuringThings newsletter.
See Intro blog here. See Part 1 here. See Part 2 here. See Part 3 here.




