This is Part 2 of The OT Security Dozen – a 12-part series on building an OT/ICS cybersecurity program for an industrial operations environment.
Note: You may have noticed that operational technology (OT)/industrial control system (ICS) cybersecurity awareness is a common theme across "The OT Security Dozen," and hence no exclusive part on awareness itself. The aim for this series is to raise awareness on each type of controls covered, and therefore is considered an essential/integral necessity across this 12-part series.
After applying Part 1: A Year of OT/ICS Cybersecurity Assessments against your industrial network environment, hopefully by now we have a prioritized list of actionable roadmaps or a baseline framework in place to build and execute an OT/ICS cybersecurity program and strategy.
OT/ICS Cybersecurity Program & Industry Standards
Relevant Reference Industry Specific Regulations
The following are OT/ICS-specific government and/or regulatory bodies and examples of regulation and guidance:
- North American Electric Reliability Corporation (NERC): A not-for-profit (i.e., Bulk Electric System’s [BES] reliability in North America). NERC has matured over the last 12 years or so and has the capability of enforcement.
- NERC Critical Infrastructure Protection (CIP): A set of cybersecurity requirements focused on OT/ICS cyber-systems that are evolving and improving continuously based on industry changes, with publicly available high-level enforcement actions.
- US: SP800-82 and NIST SP800-53.
- UK: Center of the Protection of National Infrastructure (CPNI).
- Germany: Bureau of Information Security (BSI) & Energy & Water Association (BDEW).
- APAC Critical Infrastructure (CI/CII): Regulations for Singapore, Australia, and others.
Prerequisites for OT/ICS Policy Build
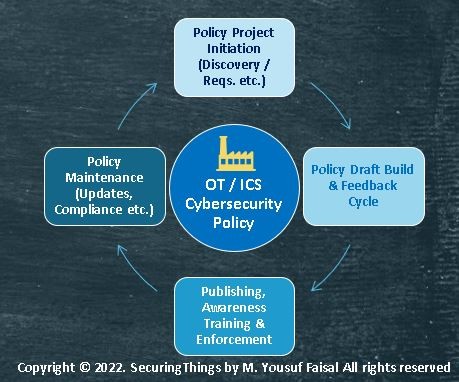
Before you initiate a policy build, there are certain prerequisites that one comes across when initiating an OT/ICS cybersecurity program. This includes establishing a repeatable and measurable process for OT/ICS cybersecurity program improvement. One should apply the following actions:
- Leadership and scope: Identify key stakeholders and executives to gain support for program sponsorship and also define a clear scope.
- Delegate ownership, build the team, and identify requirements and risks: First, appoint a person responsible for taking ownership of the program (either the chief information security officer (CISO) of the organization, and/or a dedicated OT security program lead within the OT team). Then, build a team ideally with a combination of cybersecurity and OT subject matter experts (SMEs) and resources from information technology (IT) and OT/ICS teams, as necessary. Identify business risks; architectural and vulnerability risks; and regulatory requirements while taking into account inventory and findings from earlier audits/assessments.
- Establish, enforce, and maintain policy and procedures: Follow and repeat agile practices for establishing, publishing, and enforcing policies. Maintain and updating policies through an iterative, continuous, and repeatable process cycle.
Note: According to Gartner, by 2023, "75% of organizations will restructure risk and security governance to address converged IT, OT, Internet of Things (IOT), and physical security needs, an increase from fewer than 15% in 2021.”
OT/ICS Policy as a Layer in the Defense in Depth Model
In an overall OT/ICS integrated multi-layer defense in depth (DiD) model or concept, where multiple layers of controls/defenses are tied together to reach a goal of securing things, "policy" is one layer of defense.
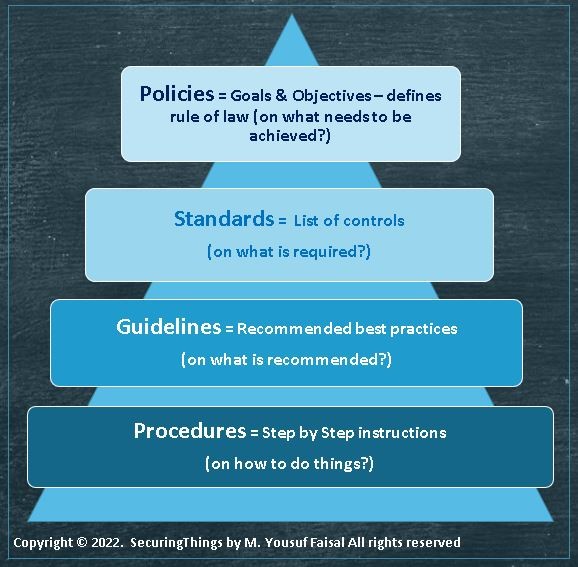
A comprehensive IT/OT cybersecurity program contains several type of documents, as shown in the figure below. Some organizations follow drafting, publishing, enforcing, and maintaining these document types and some organizations merge topic-specific elements (e.g., policy and controls. policies and procedures, and/or policy or guidance together) into different sections of these document types. IETF RFC 2119 is an often-used reference.
Note: For the purpose of this article, we’ll limit discussion at the policy level only.
Policies cover and outline high-level corporate business goals and objectives. These are applicable to all personnel, including permanent, contracted staff and vendors. These policies are further elaborated and supported via standards, guidelines, and procedure-type documents. Non-performance typically results in disciplinary actions.
OT/ICS cybersecurity policies are at the heart of building and running an OT/ICS cybersecurity strategy and program, and is closely related to OT Cybersecurity Management Systems (CSMS).
OT/ICS Policy Resources & Construct
For creating policy, there are a variety of resources to be referenced, utilized, or consumed (e.g., enterprise or IT cybersecurity policies). Take style, language, and length into account, see what's common between IT/OT, apply for OT/ICS, and work with management/IT/OT teams to define a clear scope and goals.
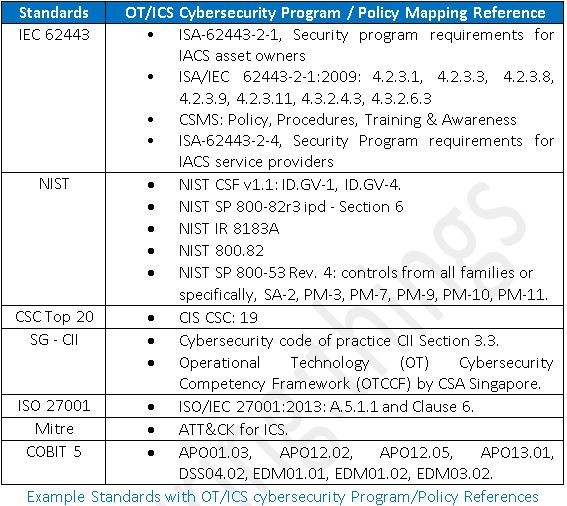
For example, the SANS policy website is a great, free place to start among many other sources. Take references from ISA/IEC 62443, NIST, CSC, NERC CIP, CSC, SG CII, ISO 27001, and other industry standards and regulatory bodies applicable for the organization.
While writing policy (as per SANS), be concise, clear, specific, and meet SMART objectives (i.e. Specific, Measurable, Achievable, Realistic, and Time-based).
Note: Policy should also cover the 5 W’s (who, what, where, when, and why); guide principles; clearly outline roles, responsibilities, and actions required to meet compliance; and offer sufficient guidance so that a specific procedure can be developed.
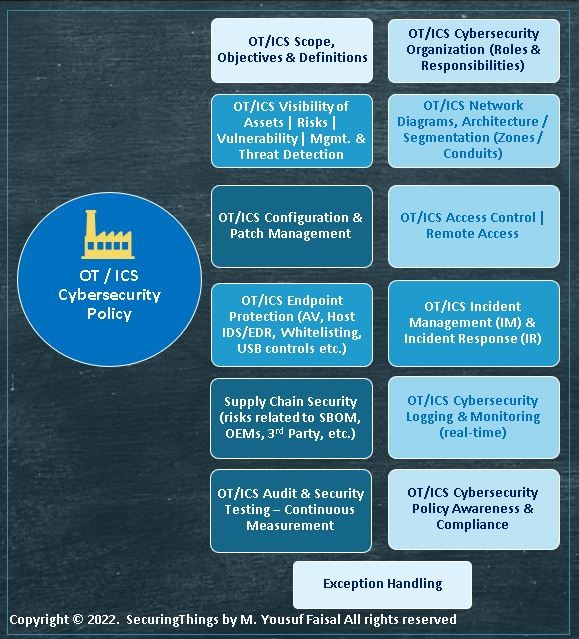
An example of an OT/ICS cybersecurity policy construct is highlighted below:
Most organizations in the industrial sector (e.g. critical infrastructure) use guidance from industry standards (e.g., NIST CSF, ISA/IEC 62443, NIST 800-53, NIST 800-82, CSC Top 20, and perhaps NIST SP 800-82r3), and/or sector-specific and/or government-specific regulations.
Policy Governance & Reviews
Compliance controls are established to ensure compliance with policies and external regulations for accuracy and reliability of business processes, ultimately measuring the level of organizational performance. Organizations must work actively to ensure and promote a culture of compliance with controls and objectives for policies to remain effective. Therefore, organizational leadership must provide sufficient funding and resources to do the following:
- Conduct awareness training: Provide adequate and frequent (mandatory) training programs with real work examples.
- Set measurable performance goals: Tie them to personnel for regulatory and policy compliance. Clearly highlight consequences and provide anonymous channels for reporting violations.
- Run an audit program: Implement and execute a comprehensive compliance/audit program to track metrics, incidents, and report results to senior management/board.
Note: Policies must be reviewed and updated periodically (at least annually or upon a major change within the business/technical environment) to be relevant and useful for the organization.
Recommendations & Key Takeaways
Remember to use the principles of SMART and the five W’s to review policies. Ensure the alignment of the policies with business needs, including industry and government regulatory requirements and proper dissemination to all parties/stakeholders with as-needed awareness training.
Policies are high-level directives that help establish a plan. Once the draft of the OT/ICS cybersecurity policy is available, you are on your way to getting buy-in from leadership and all stakeholders, getting an approval and alignment with organizational business needs. Once published, the policy should be enforced and disseminated to all required parties. Later, maintaining and updating the policy ensures its effective applicability on an ongoing basis.
Next Steps
OT/ICS cybersecurity programs and governance strategy starts with high-level directives via OT/ICS cybersecurity policy (with defined objectives and goals). After, from a governance perspective, you could think of establishing an OT/ICS CSMS.
A version of this article originally appeared on LinkedIn. The author will be first featuring the series on this platform and encourages everyone to follow along in the SecuringThings newsletter.
See Intro blog here. See Part 1 here. See Part 3 here. See Part 4 here.