Misconceptions about ICS/OT cybersecurity are stubborn. This "mythbusting" blog series dispels five common myths related to ICS cybersecurity. Catch up on previous entries if you're interested:
- Common ICS Cybersecurity Myth #1: The Air Gap
- Common ICS Cybersecurity Myth #2: Proprietary Systems and Protocols
- Common ICS Cybersecurity Myth #3: The Unbreachable Firewall
- Common ICS Cybersecurity Myth #4: Serial Communication
Now, let's dive in.
ICS Cybersecurity Myth #5
Why would someone even bother to attack smart grids or industrial networks? Many people believe that attackers are usually financially motivated, and therefore, that there is not much to gain by attacking industrial networks
Contrary to the common belief that attackers are primarily financially motivated, and that there is not much for them to gain by attacking an industrial network, there could be many reasons why hackers would seek to attack and gain access to industrial networks—especially critical infrastructure such as electricity, gas, and water.
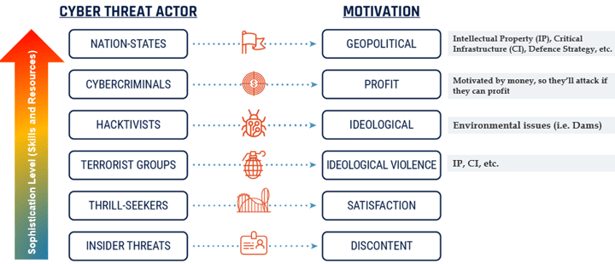 Image source: Canadian Centre for Cyber Security
Image source: Canadian Centre for Cyber Security
Cybercriminals are financially motivated, but nation states and hacktivists may have different motives beyond the financial. State-sponsored actors and hacktivists may want to gain access to vulnerable critical infrastructure or defense strategy without causing immediate damage, and use their access to other nations’ critical infrastructure to influence policies and negotiations—or they may want to cause damage or outages during potential war situations to bring about economic impacts. (All of these are hypothetical—but feasible—scenarios.)
Busting ICS Cybersecurity Myth #5
This is an insightful report that highlights various actors that are motivated to attack ICS and the vectors they leverage for initial entry into ICS.
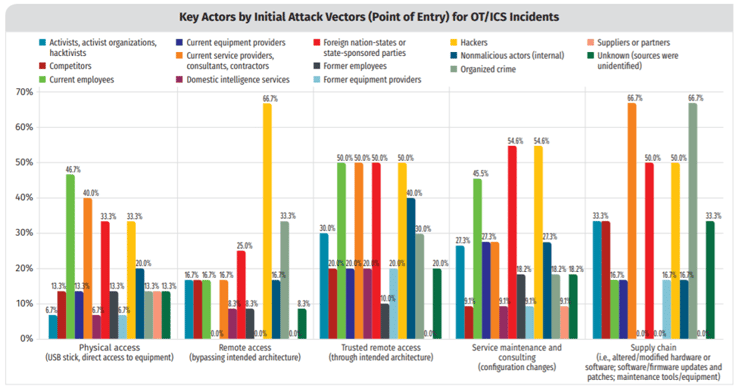 Image source: SANS 2019 State of OT/ICS Cybersecurity Survey
Image source: SANS 2019 State of OT/ICS Cybersecurity Survey
The cyber threat landscape is always growing and changing, and attackers are targeting ICS and critical infrastructures.
Below is a partial list (2010-2020) of ICS-related cyber incidents:
|
2010 |
Stuxnet attack ruined almost 20% of Iran’s nuclear centrifuges |
|
2013 |
Cyberattack on a German steel mill resulted in massive physical and equipment damages |
|
2015 |
BlackEnergy3 cyberattack on Ukrainian power utilities caused power loss for more than 225,000 customers |
|
2017 |
WannaCry attack affected 200,000+ systems in 150 countries—although not explicitly designed to target ICS, it impacted ICS as well |
|
2017 |
NotPetya attack prevented Maersk from locating and routing shipments, caused up to EUR 300 million in losses (public reports) |
|
2018 |
Restoration from a cyberattack on an Italy-based oil company took more than a week |
|
2019 |
Cyberattack on Norsk Hydro caused aluminum production shutdown, resulting in financial loss of up to 75 million USD |
|
2020 |
Ransomware attack on a US natural gas company caused a gas pipeline to be shut down for two days |
Stay tuned for the final part in this series, in which we identify major current trends in ICS cybersecurity and come up with lessons learned.
Interested in reading even more articles like this? Subscribe to the ISAGCA blog and receive weekly emails with links to the latest thought leadership, tips, research, and other insights from automation cybersecurity leaders.




